ESET Endpoint Security for macOS 6.9 Bruksanvisning
- Typ
- Bruksanvisning

Copyright ©2020 by ESET, spol. s r. o.
ESET Endpoint Security for macOS was developed by ESET, spol. s r. o.
For more information visit www.eset.com.
All rights reserved. No part of this documentation may be reproduced, stored in a retrieval system or transmitted in
any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise without
permission in writing from the author.
ESET, spol. s r. o. reserves the right to change any of the described application software without prior notice.
Worldwide Customer Support: support.eset.com
REV. 2020-07-27

1 ESET Endpoint Security for macOS 1 .................................................................................................
1.1 Nyheter i version 6 1 ..................................................................................................................................
1.2 Systemkrav 2 ...............................................................................................................................................
2 Användare som ansluter via ESET Security Management Center 2 .................................
3 Installation 3 .....................................................................................................................................................
3.1 Typisk installation 4 ...................................................................................................................................
3.2 Anpassad installation 4 .............................................................................................................................
3.3 Fjärrinstallation 7 .......................................................................................................................................
4 Produktaktivering 7 ......................................................................................................................................
5 Avinstallation 9 ...............................................................................................................................................
6 Grundläggande översikt 9 ........................................................................................................................
6.1 Tangentbordsgenvägar 9 ..........................................................................................................................
6.2 Kontrollera systemets funktion 10 ..........................................................................................................
6.3 Vad gör jag om programmet inte fungerar 10 .......................................................................................
7 Datorskydd 11 ..................................................................................................................................................
7.1 Skydd mot virus och spionprogram 11 ....................................................................................................
7.1.1 Allmänt 11 .................................................................................................................................................
7.1.1.1 Undantag 11 ............................................................................................................................................
7.1.2 Uppstartsskydd 12 .......................................................................................................................................
7.1.3 Skydd av filsystemet i realtid 12 ......................................................................................................................
7.1.3.1 Avancerade alternativ 13 ............................................................................................................................
7.1.3.2 När konfigurationen för realtidsskydd bör ändras 13 ..........................................................................................
7.1.3.3 Kontrollera realtidsskyddet 13 ......................................................................................................................
7.1.3.4 Vad gör jag om realtidsskyddet inte fungerar? 14 ..............................................................................................
7.1.4 Genomsökning av datorn 14 ..........................................................................................................................
7.1.4.1 Typ av genomsökning 15 ............................................................................................................................
7.1.4.1.1 Smart genomsökning 15 ...........................................................................................................................
7.1.4.1.2 Anpassad genomsökning 15 ......................................................................................................................
7.1.4.2 Genomsökningsobjekt 16 ............................................................................................................................
7.1.4.3 Genomsökningsprofiler 16 ...........................................................................................................................
7.1.5 Parameterinställningar för ThreatSense-motorn 17 ...............................................................................................
7.1.5.1 Objekt 18 ................................................................................................................................................
7.1.5.2 Alternativ 18 ............................................................................................................................................
7.1.5.3 Rensning 18 ............................................................................................................................................
7.1.5.4 Undantag 19 ............................................................................................................................................
7.1.5.5 Begränsningar 19 .....................................................................................................................................
7.1.5.6 Övriga 20 ................................................................................................................................................
7.1.6 En infiltration identifieras 20 ..........................................................................................................................
7.2 Webb- och e-postskydd 21 ........................................................................................................................
7.2.1 Webbåtkomstskydd 21 .................................................................................................................................
7.2.1.1 Portar 21 ................................................................................................................................................
7.2.1.2 URL-listor 21 ............................................................................................................................................
7.2.2 E-postskydd 22 ...........................................................................................................................................
7.2.2.1 Kontroll av POP3-protokoll 23 .......................................................................................................................
7.2.2.2 Kontroll av IMAP-protokoll 23 .......................................................................................................................
7.3 Skydd mot nätfiske 23 ...............................................................................................................................
8 Brandvägg 24 ...................................................................................................................................................
8.1 Filtreringslägen 24 ......................................................................................................................................
8.2 Brandväggsregler 25 ..................................................................................................................................
8.2.1 Skapa nya regler 26 .....................................................................................................................................
8.3 Brandväggszoner 26 ...................................................................................................................................
8.4 Brandväggsprofiler 26 ................................................................................................................................
8.5 Brandväggsloggar 26 .................................................................................................................................

9 Enhetskontroll 27 ...........................................................................................................................................
9.1 Regelredigerare 27 .....................................................................................................................................
10 Webbkontroll 29 ...........................................................................................................................................
11 Verktyg 31 .......................................................................................................................................................
11.1 Loggfiler 31 ................................................................................................................................................
11.1.1 Loggunderhåll 31 .......................................................................................................................................
11.1.2 Loggfiltrering 32 ........................................................................................................................................
11.2 Schemaläggaren 33 ..................................................................................................................................
11.2.1 Skapa nya aktiviteter 34 ..............................................................................................................................
11.2.2 Skapa en användardefinierad aktivitet 35 ........................................................................................................
11.3 LiveGrid® 36 ..............................................................................................................................................
11.3.1 Misstänkta filer 36 .....................................................................................................................................
11.4 Karantän 37 ...............................................................................................................................................
11.4.1 Sätta filer i karantän 38 ...............................................................................................................................
11.4.2 Återställa en fil i karantän 38 ........................................................................................................................
11.4.3 Skicka en fil från karantän 38 ........................................................................................................................
11.5 Behörigheter 38 ........................................................................................................................................
11.6 Presentationsläge 38 ...............................................................................................................................
11.7 Processer som körs 39 .............................................................................................................................
12 Användargränssnitt 40 .............................................................................................................................
12.1 Varningar och meddelanden 40 .............................................................................................................
12.1.1 Visa varningar 41 ......................................................................................................................................
12.1.2 Skyddsstatusar 41 .....................................................................................................................................
12.2 Kontextmeny 41 ........................................................................................................................................
13 Uppdatera 42 .................................................................................................................................................
13.1 Inställning av uppdateringar 42 .............................................................................................................
13.1.1 Avancerade alternativ 44 .............................................................................................................................
13.2 Skapa uppdateringsaktiviteter 44 .........................................................................................................
13.3 Systemuppdateringar 45 .........................................................................................................................
13.4 Importera och exportera inställningar 46 ............................................................................................
13.5 Inställning av proxyserver 46 .................................................................................................................
13.6 Delad lokal cache 47 ................................................................................................................................
14 End User License Agreement 47 .........................................................................................................
15 Sekretesspolicy 53 ......................................................................................................................................

1
ESET Endpoint Security for macOS
ESET Endpoint Security for macOS 6 representerar ett nytt förhållningssätt till integrerad datasäkerhet. Den
senaste versionen av genomsökningsmotorn ThreatSense®, i kombination med vår skräddarsydda brandvägg,
använder snabbhet och noggrannhet för att skydda datorn. Resultatet är ett intelligent system som är
oupphörligen vaksamt mot attacker och skadlig programvara som kan utgöra en fara för din dator.
ESET Endpoint Security for macOS 6 är en fullständig säkerhetslösning utvecklad med vår långa erfarenhet av att
kombinera maximalt skydd och minimal systembelastning. Den avancerade tekniken som bygger på artificiell
intelligens kan proaktivt eliminera infiltration av virus, spionprogram, trojaner, maskar, reklamprogram, rootkit och
andra attacker från Internet utan att minska systemets prestanda eller störa din dator.
Produkten är framför allt utformad för användning på arbetsstationer i småföretags-/företagsmiljö. Den går att
använda med ESET Security Management Center 7 och gör det enkelt att hantera olika antal klientarbetsstationer,
tillämpa principer och regler, övervaka detekteringar och fjärradministrera ändringar från alla datorer anslutna till
nätverket.
Nyheter i version 6
Det grafiska användargränssnittet för ESET Endpoint Security for macOS har fått en helt ny utformning som ger
bättre översikt och en mer intuitiv användarupplevelse. Några av de många förbättringarna i version 6 inkluderar:
• Stöd för ESET Enterprise Inspector – från ESET Endpoint Security for macOS version 6.9, ESET Endpoint
Security for macOS kan anslutas med ESET Enterprise Inspector. ESET Enterprise Inspector (EEI) är ett
omfattande slutpunktsdetekterings- och responssystem med funktioner som: incidentdetektering,
incidenthantering och -respons, datainsamling, detektering av indikatorer på intrång, anomalidetektering,
beteendedetektering och policyöverträdelser. För mer information om ESET Enterprise Inspector, dess
installation och funktioner, se hjälpen för ESET Enterprise Inspector.
• Stöd för 64-bitarsarkitektur
• Personlig brandvägg – nu kan du skapa brandväggsregler direkt från loggen eller IDS (Intrusion detection
system)-meddelandefönstret och tilldela profiler till nätverksgränssnitt
• Webbkontroll – blockerar webbsidor som kan innehålla olämpligt eller stötande innehåll
• Webbåtkomstskydd – övervakar kommunikationen mellan webbläsare och fjärrservrar
• E-postskydd – ger kontroll av e-postkommunikation som tas emot via POP3- och IMAP-protokollen
• Skydd mot nätfiske – skyddar mot försök att hämta lösenord och annan känslig information genom att
begränsa åtkomsten till skadliga webbplatser som utger sig för att vara tillförlitliga
• Enhetskontroll – gör det möjligt att genomsöka, blockera eller justera utökade filter och/eller behörigheter
och välja hur användaren får åtkomst till och arbetar med externa enheter. Denna funktion är tillgänglig i
produktversion 6.1 och senare versioner.
• Presentationsläge – med det här alternativet kan du köra ESET Endpoint Security for macOS i bakgrunden
och dölja popup-fönster och schemalagda aktiviteter
• Delad lokal cache – får genomsökningar i virtualiserade miljöer att gå snabbare

2
Systemkrav
För att ESET Endpoint Security for macOS ska ge optimala prestanda bör systemet uppfylla följande krav på
maskinvara och programvara:
Systemkrav:
Processorarkitektur Intel 64-bit
Operativsystem macOS 10.12 och senare
Minne 300 MB
Ledigt diskutrymme 200 MB
Användare som ansluter via ESET Security
Management Center
ESET Security Management Center 7 är ett program som möjliggör hantering av ESET-produkter i en nätverksmiljö
från en central plats. Med åtgärdshanteringssystemet ESET Security Management Center kan du installera ESET-
säkerhetslösningar på fjärrdatorer och snabbt bemöta nya problem och hot. ESET Security Management Center ger
inget skydd mot skadlig kod i sig självt, utan förlitar sig till en ESET-säkerhetslösning i varje klient.
ESET-säkerhetslösningarna har stöd för nätverk med flera plattformstyper. Nätverket kan innehålla en kombination
av aktuella Microsoft-, Linux-baserade eller macOS-operativsystem som körs i mobila enheter (mobiltelefoner och
surfplattor).
ESET Security Management Center tillhör en ny generation fjärrhanteringssystem som skiljer sig avsevärt från
tidigare versioner av ESET Security Management Center. Eftersom arkitekturen är helt annorlunda är ESET Security
Management Center 7 endast delvis kompatibelt med ERA 6 och det finns ingen bakåtkompatibilitet med ERA 5.
Det finns dock fortfarande kompatibilitet med tidigare versioner av ESET-säkerhetsprodukter.
Tillsammans med nya ESET Security Management Center har ESET utvecklat en ny generation säkerhetsprodukter
med ett nytt licenssystem.
För att göra en fullständig distribution av portföljen med säkerhetslösningar från ESET måste följande komponenter
vara installerade (Windows- och Linux-plattformar):
• ESET Security Management Center-server
• ESET Security Management Center Webbkonsol
• ESET Management Agent
Följande stödkomponenter är valfria, men bör installeras för att programmet ska fungera så bra som möjligt i
nätverket:
• Proxy
• RD-sensor
• Apache HTTP-proxy
• Mobile Device Connector

3
ESET Security Management Center-dokumentation
Ytterligare information finns i ESET Security Management Center-onlinedokumentationen.
Installation
Installationsprogrammet för ESET Endpoint Security for macOS kan startas på två olika sätt:
• Om du installerar från installations-CD/DVD-skivan sätter du in skivan i CD/DVD-ROM-enheten och
dubbelklickar på ESET Endpoint Security for macOS-installationsikonen för att starta installationsprogrammet.
• Om du installerar från en hämtad fil, dubbelklicka på den hämtade filen för att starta installationsprogrammet.
Installationsguiden leder dig genom den grundläggande installationen. Under installationens första del söker
installationsprogrammet automatiskt online efter den senaste produktversionen. Om en nyare version hittas kan
du välja att hämta den senaste versionen innan installationen fortsätter.
Installera från .pkg-filen
Under installationen och den första starten av ESET-produkter för macOS som installeras från .pkg-
filen krävs internetåtkomst på datorn för att Apple ska kunna verifiera ESET:s kerneltillägg.
Godkänn licensavtalet för slutanvändare och välj bland följande installationstyper:
• Typisk installation
• Anpassad installation
• Fjärrinstallation

4
Typisk installation
Typisk installation innehåller konfigurationsalternativ som passar de flesta användare. Dessa inställningar ger
maximal säkerhet kombinerad med utmärkta systemprestanda. Typisk installation är standardalternativet och
rekommenderas för dem som inte har särskilda krav på vissa inställningar.
ESET LiveGrid®
ESET LiveGrid® Early Warning System hjälper till att säkerställa att ESET alltid har den senaste informationen om
nya infiltreringar för att snabbt skydda kundernas datorer. LiveGrid®-systemet skickar nya hot till ESET:s
viruslaboratorium, där de analyseras och behandlas. Klicka på Inställningar och ändra inställningarna för att
skicka in misstänkta filer. Se LiveGrid® för ytterligare information. Om ESET LiveGrid® inte är aktiverat visar ESET
Endpoint Security for macOS en säkerhetsvarning.
Potentiellt oönskade program
Det sista steget i installationsprocessen är konfiguration av identifiering av Potentiellt oönskade program.
Dessa program är inte nödvändigtvis skadliga, men de kan ändå påverka operativsystemets prestanda negativt.
Potentiellt oönskade program utgör ofta en del av installationen av andra program du väljer att hämta och det
finns en risk att de installeras obemärkt. Även om dessa program vanligen visar ett meddelande under
installationen, kan de enkelt installeras utan ditt samtycke.
Efter den första installationen av ESET Endpoint Security for macOS:
1. I macOS 10.13 och senare får du meddelandet Ett systemtillägg har blockerats från systemet och
meddelandet Datorn skyddas inte från ESET Endpoint Security for macOS. För att aktivera alla funktioner i
ESET Endpoint Security for macOS måste du tillåta kernel-tillägg på enheten. Om du vill tillåta kernel-tillägg på
enheten navigerar du till Systeminställningar > Säkerhet och sekretess och klickar på Tillåt för att tillåta
systemprogram från utvecklaren ESET, spol. s.r.o. Du kan läsa mer i vår artikel i kunskapsbasen.
2. I macOS 10.14 får du meddelandet Datorn skyddas delvis från ESET Endpoint Security for macOS. För att
aktivera alla funktioner i ESET Endpoint Security for macOS måste du ge Full diskåtkomst till ESET Endpoint
Security for macOS. Klicka på Öppna systeminställningar > Säkerhet och sekretess. Öppna fliken
Sekretess och välj alternativet Full diskåtkomst. Klicka på låsikonen för att aktivera redigering. Klicka på
plusikonen och välj ESET Endpoint Security for macOS-programmet. Ett meddelande om att starta om datorn
visas. Klicka på Senare. Starta inte om datorn nu. Klicka på Starta igen i ESET Endpoint Security for macOS-
meddelandefönstret eller starta om datorn. Du kan läsa mer i vår artikel i kunskapsbasen.
Utför en genomsökning av datorn efter skadlig kod när ESET Endpoint Security for macOS installerats. I
programmets huvudfönster klickar du på Genomsökning av datorn > Smart genomsökning. Mer information
om genomsökning av datorn på begäran finns i avsnittet Genomsökning av datorn på begäran.
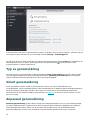
Anpassad installation
Anpassade installation är avsedd för användare som vill ändra de avancerade inställningarna under installationen.
Programkomponenter

5
ESET Endpoint Security for macOS kan installeras utan vissa av dess kärnkomponenter (exempelvis webb- och e-
postskydd). Avmarkera kryssrutan intill en produktkomponent om du vill undanta den från installationen.
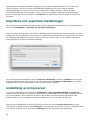
Proxyserver
Använder du en proxyserver går det att definiera parametrarna genom att välja alternativet Jag använder
proxyserver. Ange proxyserverns IP- eller URL-adress i fältet Adress i nästa fönster. Ange porten där
proxyservern tar emot anslutningar i fältet Port (3128 är standard). Om proxyservern kräver autentisering, ange
ett giltigt Användarnamn och Lösenord för åtkomst till proxyservern. Om du inte använder en proxyserver väljer
du Använd inte en proxyserver. Om du inte är säker på om du använder en proxyserver eller inte går det att
använda de aktuella systeminställningarna genom att välja Använd systeminställningarna (rekommenderas).
Behörigheter
I nästa steg går det att definiera behöriga användare eller grupper som får ändra programinställningarna. Välj
användarna på listan med användare till vänster och Lägg till dem på listan Behöriga användare. Om du vill
visa alla systemanvändare markerar du Visa alla användare. Lämnar du listan Behöriga användare tom, anses
alla användare vara behöriga.
ESET LiveGrid®
ESET LiveGrid® Early Warning System hjälper till att säkerställa att ESET alltid har den senaste informationen om
nya infiltreringar för att snabbt skydda kundernas datorer. Systemet tillåter att nya hot skickas till ESET:s
viruslaboratorium, där de analyseras och behandlas. Klicka på Inställningar och ändra inställningarna för att
skicka in misstänkta filer. Se LiveGrid® för ytterligare information. Om ESET LiveGrid® inte är aktiverat visar ESET
Endpoint Security for macOS en säkerhetsvarning.
Potentiellt oönskade program
Nästa steg i installationsprocessen är konfiguration av identifiering av Potentiellt oönskade program. Dessa
program är inte nödvändigtvis skadliga, men de kan ändå påverka operativsystemets prestanda negativt. De utgör
ofta en del av installationen av andra program du hämtar och det finns en risk att de installeras obemärkt. Även
om dessa program vanligen visar ett meddelande under installationen, kan de enkelt installeras utan ditt
samtycke.
Brandvägg
Välj ett filtreringsläge för brandväggen. För ytterligare information, se Filtreringslägen.
Efter den första installationen av ESET Endpoint Security for macOS:
1. I macOS 10.13 och senare får du meddelandet Ett systemtillägg har blockerats från systemet och
meddelandet Datorn skyddas inte från ESET Endpoint Security for macOS. För att aktivera alla funktioner i
ESET Endpoint Security for macOS måste du tillåta kernel-tillägg på enheten. Om du vill tillåta kernel-tillägg på
enheten navigerar du till Systeminställningar > Säkerhet och sekretess och klickar på Tillåt för att tillåta
systemprogram från utvecklaren ESET, spol. s.r.o. Du kan läsa mer i vår artikel i kunskapsbasen.
2. I macOS 10.14 får du meddelandet Datorn skyddas delvis från ESET Endpoint Security for macOS. För att
aktivera alla funktioner i ESET Endpoint Security for macOS måste du ge Full diskåtkomst till ESET Endpoint

6
Security for macOS. Klicka på Öppna systeminställningar > Säkerhet och sekretess. Öppna fliken
Sekretess och välj alternativet Full diskåtkomst. Klicka på låsikonen för att aktivera redigering. Klicka på
plusikonen och välj ESET Endpoint Security for macOS-programmet. Ett meddelande om att starta om datorn
visas. Klicka på Senare. Starta inte om datorn nu. Klicka på Starta igen i ESET Endpoint Security for macOS-
meddelandefönstret eller starta om datorn. Du kan läsa mer i vår artikel i kunskapsbasen.
Utför en genomsökning av datorn efter skadlig kod när ESET Endpoint Security for macOS installerats. I
programmets huvudfönster klickar du på Genomsökning av datorn > Smart genomsökning. Mer information
om genomsökning av datorn på begäran finns i avsnittet Genomsökning av datorn på begäran.
Fjärrinstallation
Före installationen
Innan ESET Endpoint Security for macOS installeras på macOS 10.13 och senare rekommenderar vi att du tillåter
ESET-kerneltillägg och, på macOS 10.14 och senare, även tillåter fullständig diskåtkomst på måldatorerna. Om
dessa alternativ tillåts efter installationen får användare meddelandena Ett systemtillägg har blockerats och
Datorn skyddas delvis tills ESET-kerneltillägg och fullständig diskåtkomst har tillåtits.
För att tillåta ESET-kerneltillägg och fullständig diskåtkomst via fjärrstyrning behöver datorn vara registrerad på
MDM-servern (Mobile Device Management), till exempel Jamf.
Tillåta ESET-kerneltillägg
• Kerneltillägg behöver endast tillåtas vid den första installationen av ESET Endpoint Security for macOS. Så här
gör du för att fjärrtillåta kerneltillägg på enheten:
oOm Jamf används som MDM följer du vår artikel i kunskapsbasen.
oOm en annan MDM används laddar du ned .plist-konfigurationsprofilen. Generera två UUID:er med valfri
UUID-generator och använd en textredigerare för att ersätta strängar med texten infoga UUID 1 här och
infoga UUID 2 här i den hämtade konfigurationsprofilen. Distribuera .plist-filen med konfigurationsprofilen
med hjälp av MDM-servern. Datorn behöver vara registrerad på MDM-servern för att konfigurationsprofiler ska
kunna distribueras till dessa datorer.
Tillåta fullständig diskåtkomst
• I macOS 10.14 får du meddelandet Datorn skyddas delvis från ESET Endpoint Security for macOS efter
installationen. Om du vill komma åt alla funktioner i ESET Endpoint Security for macOS och hindra aviseringen
från att visas behöver du tillåta fullständig diskåtkomst för ESET Endpoint Security for macOS innan
produkten installeras. Så här gör du för att fjärrtillåta fullständig diskåtkomst:
oOm Jamf används som MDM följer du vår artikel i kunskapsbasen.
oOm du vill tillåta fullständig diskåtkomst via fjärrstyrning hämtar du .plist-konfigurationsprofilen. Generera
två UUID:er med valfri UUID-generator och använd en textredigerare för att ersätta strängar med texten
infoga UUID 1 här och infoga UUID 2 här i den hämtade konfigurationsprofilen. Distribuera .plist-filen med
konfigurationsprofilen med hjälp av MDM-servern. Datorn behöver vara registrerad på MDM-servern för att
konfigurationsprofiler ska kunna distribueras till dessa datorer.
Installation
Det går att fjärrinstallera ESET Endpoint Security for macOS med hjälp av ESET Security Management Center från
webbkonsolen genom att skapa en åtgärd för programinstallation.
För utförliga anvisningar besöker du:
• Hjälpavsnittet om att skapa åtgärder för ERA-programinstallation på webben
• Artikeln Distribuera eller uppgradera ESET-slutpunktslösningar med ERA i kunskapsbasen

7
• Hjälpavsnittet om att skapa åtgärder för ESET Security Management Center-programinstallation på webben
Efter installation
Om du inte har tillåtit ESET-kerneltillägg och fullständig diskåtkomst:
Tillåta ESET-kerneltillägg
Efter den första installationen av ESET Endpoint Security for macOS:
1. I macOS 10.13 och senare får du meddelandet Ett systemtillägg har blockerats från systemet och
meddelandet Datorn skyddas inte från ESET Endpoint Security for macOS. Om du vill komma åt alla
funktioner i ESET Endpoint Security for macOS behöver du tillåta kerneltillägg på datorn.
a.Om du vill tillåta kerneltillägg på enheten manuellt navigerar du till Systeminställningar > Säkerhet
och sekretess och klickar på Tillåt för att tillåta systemprogram från utvecklaren ESET, spol. s.r.o. u kan
läsa mer i vår artikel i kunskapsbasen.
b.Så här gör du för att fjärrtillåta kerneltillägg på enheten:
i.Om Jamf används som MDM följer du vår artikel i kunskapsbasen.
ii.Om en annan MDM används laddar du ned .plist-konfigurationsprofilen. Generera två UUID:er med
valfri UUID-generator och använd en textredigerare för att ersätta strängar med texten infoga UUID 1
här och infoga UUID 2 här i den hämtade konfigurationsprofilen. Distribuera .plist-filen med
konfigurationsprofilen med hjälp av MDM-servern. Datorn behöver vara registrerad på MDM-servern för
att konfigurationsprofiler ska kunna distribueras till dessa datorer.
Tillåta fullständig diskåtkomst
• I macOS 10.14 får du meddelandet Datorn skyddas delvis från ESET Endpoint Security for macOS. Om du
vill komma åt alla funktioner i ESET Endpoint Security for macOS behöver du tillåta fullständig diskåtkomst
för ESET Endpoint Security for macOS. Så här gör du för att fjärrtillåta fullständig diskåtkomst:
oOm Jamf används som MDM följer du vår artikel i kunskapsbasen.
oOm du vill tillåta fullständig diskåtkomst via fjärrstyrning hämtar du .plist-konfigurationsprofilen. Generera
två UUID:er med valfri UUID-generator och använd en textredigerare för att ersätta strängar med texten
infoga UUID 1 här och infoga UUID 2 här i den hämtade konfigurationsprofilen. Distribuera .plist-filen med
konfigurationsprofilen med hjälp av MDM-servern. Datorn behöver vara registrerad på MDM-servern för att
konfigurationsprofiler ska kunna distribueras till dessa datorer.
Du kan även tillåta fullständig diskåtkomst manuellt. För utförliga anvisningar besöker du vår artikel i
kunskapsbasen.
Produktaktivering
När installationen är slutförd ombeds du aktivera produkten. Det finns flera aktiveringsmetoder som kan användas.
Tillgängligheten för en viss aktiveringsmetod i aktiveringsfönstret kan bero på land och distributionssätt (CD/DVD,
ESET-webbsida osv.) för produkten.
Om du vill aktivera ditt exemplar av ESET Endpoint Security for macOS direkt från programmet klickar du på ESET
Endpoint Security for macOS-ikonen i macOS-menyfältet (överst på skärmen) och klickar på
Produktaktivering. Du kan även aktivera produkten via huvudmenyn under Hjälp > Hantera licens eller
Skyddsstatus > Aktivera produkt.

8
ESET Endpoint Security for macOS kan aktiveras på något av följande sätt:
• Aktivera med licensnyckel – en unik sträng i formatet XXXX-XXXX-XXXX-XXXX-XXXX som används för
identifiering av licensägaren och aktivering av licensen. Du hittar din licensnyckel i e-postmeddelandet som du
fick efter köpet eller på licenskortet i förpackningen.
• Säkerhetsadministratörskonto – ett konto som skapas på ESET License Administrator-portalen med
uppgifter (e-postadress och lösenord). Med den här metoden kan du hantera flera licenser från en plats.
• Offlinelicens – en automatiskt genererad fil som överförs till ESET-produkten för att tillhandahålla
licensinformation. Offlinelicensfilen genereras från ESET License Administrator-portalen och används i miljöer där
programmet inte kan ansluta till licensutfärdaren.
Du kan även aktivera klienten senare om datorn ingår i ett hanterat nätverk och administratören kommer att
aktivera produkten med ESET Remote Administrator.
Tyst aktivering
ESET Remote Administrator kan aktivera klientdatorer tyst med hjälp av licenser som gjorts
tillgängliga av administratören.
I ESET Endpoint Security for macOS version 6.3.85.0 (eller senare) kan produkten aktiveras med Terminal. Om du
vill göra detta använder du följande kommando:
sudo ./esets_daemon --wait-respond --activate key=XXXX-XXXX-XXXX-XXXX-XXXX

9
Byt ut XXXX-XXXX-XXXX-XXXX-XXXX mot en licensnyckel som redan har använts för aktivering av ESET Endpoint
Security for macOS eller registrerats i ESET License Administrator. Kommandot returnerar antingen statusen "OK"
eller ett fel om aktiveringen misslyckas.
Avinstallation
Avinstallationsprogrammet för ESET Endpoint Security for macOS kan startas på flera olika sätt:
• sätt in ESET Endpoint Security for macOS-installations-CD/DVD-skivan i datorn, öppna den från skrivbordet
eller Finder-fönstret och dubbelklicka på Avinstallera
• öppna ESET Endpoint Security for macOS-installationsfilen (.dmg) och dubbelklicka på Avinstallera,
• starta Finder, öppna mappen Program på hårddisken, tryck på CTRL och klicka på ESET Endpoint Security
for macOS-symbolen och välj Visa paketets innehåll. Öppna mappen Contents > Helpers och dubbelklicka
på Uninstaller-ikonen.
Grundläggande översikt
ESET Endpoint Security for macOS huvudfönster är indelat i två delar. Det primära fönstret till höger visar
information som motsvarar alternativt som valts i huvudmenyn till vänster.
Följande avsnitt är åtkomliga via huvudmenyn:
• Skyddsstatus – ger information om skyddsstatus för datorn, brandvägg samt skydd för webb och e-post.
• Genomsökning av datorn – i det här avsnittet kan du konfigurera och starta en genomsökning av datorn.
• Uppdatering – visar information om moduluppdateringar.
• Inställningar – i det här avsnittet kan du justera datorns säkerhetsnivå.
• Verktyg – ger åtkomst till Loggfiler, Schemaläggaren, Karantän, Processer som körs och andra
programfunktioner.
• Hjälp – visar åtkomst till hjälpfiler, kunskapsbas på Internet, supportformulär och ytterligare
programinformation.
Tangentbordsgenvägar
Tangentbordsgenvägar som kan användas med ESET Endpoint Security for macOS:
• cmd+, - visar ESET Endpoint Security for macOS-preferenser,
• cmd+O - ändrar storlek på huvudfönstret i ESET Endpoint Security for macOS till standardstorlek och flyttar
det till bildskärmens mitt,
• cmd+Q - döljer ESET Endpoint Security for macOS-GUI-huvudfönstret. Du kan öppna det genom att klicka på
ESET Endpoint Security for macOS-ikonen i macOS-menyfältet (överst på skärmen),
• cmd+W - stänger ESET Endpoint Security for macOS-GUI-huvudfönstret.

10
Följande tangentbordsgenvägar fungerar endast om alternativet Använd standardmeny är aktiverat i
Inställningar > Ange programinställningar... > Gränssnitt:
• cmd+alt+L – öppnar avsnittet Loggfiler,
• cmd+alt+S – öppnar avsnittet Schemaläggare,
• cmd+alt+Q – öppnar avsnittet Karantän.
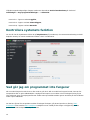
Kontrollera systemets funktion
Om du vill visa din skyddsstatus klickar du på Skyddsstatus på huvudmenyn. En statussammanfattning om ESET
Endpoint Security for macOS-modulernas funktion visas i huvudfönstret.
Vad gör jag om programmet inte fungerar
När en modul fungerar korrekt visas en ikon med en grön bock. När en modul inte fungerar korrekt visas ett rött
utropstecken eller en gul meddelandeikon. Ytterligare information om modulen och en föreslagen lösning för att
lösa problemet visas i huvudprogramfönstret. Ändra status på enskilda moduler genom att klicka på den blå länken
under varje meddelande.
Om det inte går att lösa ett problem med den föreslagna lösningen, går det att leta efter en lösning i ESET
kunskapsbas eller kontakta ESET kundtjänst. Kundtjänst svarar snabbt på dina frågor och hjälper dig att lösa
problem med ESET Endpoint Security for macOS.

11
Datorskydd
Datorkonfigurationen finns under Inställningar > Dator. Den visar status för Skydd av filsystemet i realtid.
Stäng av enskilda moduler genom att ställa on den önskade modulen till INAKTIVERAD. Observera att detta kan
minska skyddsnivån för datorn. Klicka på Inställningar för att öppna detaljerade inställningar för varje modul.
Skydd mot virus och spionprogram
Antivirusskyddet skyddar mot skadliga systemattacker genom att ändra filer som utgör potentiella hot. Om ett hot
med skadlig kod identifieras eliminerar antivirusmodulen det genom att först blockera och därefter rensa, ta bort
eller flytta det till karantän.
Allmänt
I avsnittet Allmänt (Inställningar > Ange programinställningar... > Allmänt) kan du aktivera identifiering av
följande programtyper:
• Potentiellt oönskade program – dessa program är kanske inte avsedda att vara skadliga, men de påverkar
ändå datorns prestanda negativt. Sådana program kräver vanligtvis ditt godkännande för att kunna installeras.
Om de finns på din dator fungerar systemet på ett annat sätt (jämfört med innan de installerades). De vanligaste
förändringarna är oönskade popup-fönster, aktivering och körning av dolda processer, ökad användning av
systemresurser, ändringar i sökresultat och program som kommunicerar med fjärrservrar.
• Potentiellt farliga program – dessa program är kommersiella, legitima program som kan utnyttjas i skadliga
syften om de installerades utan användarens kännedom. Klassificeringen inkluderar program som t.ex. verktyg
för fjärråtkomst, varför alternativet är inaktiverat som standard.
• Misstänkta program – inkluderar program som komprimerats med komprimeringsprogram eller skydd.
Dessa typer av skydd utnyttjas ofta av skadlig kod för att undvika upptäckt. Komprimeringsprogram är en
självuppackande körbar fil som inkluderar flera sorters skadlig kod i ett enda paket. De vanligaste
komprimeringsprogrammen är UPX, PE_Compact, PKLite och ASPack. Samma skadliga kod upptäcks på olika sätt
när den komprimeras med ett annat komprimeringsprogram. Komprimeringsprogram har även förmågan att
förändra sina "signaturer" över tid, vilket gör det svårare att identifiera och ta bort skadlig kod.
Om du vill ställa in Filsystem eller undantag för webb och e-post klickar du på Inställningar.
Undantag
I avsnittet Undantag kan du undanta vissa filer/mappar, program eller IP/IPv6-adresser från genomsökning.
Filer och mappar på fliken Filsystem undantas från alla genomsökare: start, realtid och på begäran
(datorgenomsökning).
• Sökväg - sökväg till undantagna filer och mappar
• Hot - om det finns ett namn på ett hot intill en undantagen fil betyder detta att filen endast är undantagen för
det angivna hotet (dvs. inte fullständigt undantagen). Om filen vid ett senare tillfälle infekteras av annan skadlig

12
kod detekteras denna skadliga kod av antivirusmodulen.
• – skapar ett nytt undantag. Ange sökvägen till ett objekt (det går även att använda jokertecknen * och ?)
eller välj mappen eller filen i trädstrukturen.
• – tar bort valda poster
• Standard – återställer exkluderingar till senast sparade status.
På fliken Webb och e-post går det att undanta vissa program eller IP/IPv6-adresser från
protokollgenomsökning.
Uppstartsskydd
Kontroll av filer som startas genomsöker automatiskt filer vid systemstart. Som standard körs denna
genomsökning regelbundet som en schemalagd uppgift när en användare loggat in eller efter en uppdaterig av
modulerna. Du kan ändra ThreatSense-motons parameterinställningar för genomsökning vid start genom att klicka
på Inställningar. Du kan läsa mer om ThreatSense-motorns inställningar i det här avsnittet.
Skydd av filsystemet i realtid
Realtidsskyddet av filsystemet kontrollerar alla mediatyper och olika händelser utlöser genomsökningen. Med
ThreatSense-tekniken (beskrivs i Parameterinställningar för ThreatSense-motorn) kan realtidsskyddet av
filsystemet variera för nya och befintliga filer. Nyligen skapade filer kan kontrolleras mer exakt.
Som standard genomsöks filerna när de öppnas, skapas eller körs. Vi rekommenderar att behålla
standardinställningarna eftersom de ger datorn ett maximalt realtidsskydd. Realtidsskyddet startas när systemet
startas och ger oavbruten genomsökning. I specialfall (exempelvis om det finns en konflikt med ett annat
realtidsskydd) går det att avbryta realtidsskyddet genom att klicka på ESET Endpoint Security for macOS-ikonen
i menyfältet (högst upp på skärmen) och välja Inaktivera skydd av filsystemet i realtid. Realtidsskyddet av
filsystemet går även att stänga av från programmets huvudfönster (klicka på Inställningar > Dator och ställ in
Skydd av filsystemet i realtid på INAKTIVERAT).
Följande medietyper kan undantas från Real-time-skannern:
• Lokala enheter - hårddiskar i systemet
• Flyttbara medier - CD, DVD, USB-media, Bluetooth-enheter osv.
• Nätverksmedier - alla mappade enheter
Vi rekommenderar att du använder standardinställningarna och endast ändra undantag för genomsökning i
speciella fall, till exempel om kontroll av vissa media gör att dataöverföring går betydligt långsammare.
Gå till Inställningar > Ange programinställningar... för att ändra realtidsskyddets avancerade inställningar
(eller tryck på cmd+, > Realtidsskydd och klicka på Inställningar... intill Avancerade alternativ (beskrivs i
Avancerade genomsökningsalternativ).

13
Avancerade alternativ
I det här fönstret kan du definiera vilka objekttyper som ska genomsökas av ThreatSense-motorn. Om du vill ha
mer information om självuppackande arkiv, internt packade filer och avancerad heuristik, se
Parameterinställningar för ThreatSense-motorn.
Vi rekommenderar inte att göra ändringar i avsnittet Standardinställningar för arkiv om det inte krävs för att
lösa ett visst problem, eftersom högre värden för nästlade arkiv kan försämra systemets prestanda.
Ytterligare ThreatSense-parametrar för filer som har körts – som standard används Avancerad heuristik
när filer körs. Vi rekommenderar starkt att Smart optimering och ESET LiveGrid® hålls aktiverade så att systemets
prestanda inte påverkas lika mycket.
Öka nätverksvolymernas kompatibilitet – det här alternativet ökar prestanda vid åtkomst till filer över
nätverket. Det bör aktiveras om det går långsamt att komma åt nätverksenheter. Funktionen använder
samordnaren för systemfiler i OS X 10.10 och senare. Tänk på att inte alla program har stöd för filsamordnaren, till
exempel saknar Microsoft Word 2011 stöd för det, medan Word 2016 har stöd för det.
När konfigurationen för realtidsskydd bör ändras
Realtidsskyddet är den viktigaste komponenten för att upprätthålla ett säkert system. Var försiktig vid ändring av
realtidsskyddets parametrar. Vi rekommenderar att endast ändra dessa inställningar under vissa förutsättningar.
Om det till exempel uppstår en konflikt med ett program eller en realtidsskanner i ett annat antivirusprogram.
Efter installation av ESET Endpoint Security for macOS optimeras alla inställningar så att användarna får ett
maximalt systemskydd. Återställ standardinställningarna genom att klicka på knappen Standard längst ned i
fönstret Realtidsskydd (Inställningar > Ange programinställningar... > Realtidsskydd).
Kontrollera realtidsskyddet
Kontrollera att realtidsskyddet fungerar och detekterar virus genom att använda testfilen eicar.com. Denna testfil
är en speciell och ofarlig fil som upptäcks av alla antivirusprogram. Filen skapades av EICAR (European Institute for
Computer Antivirus Research) för att testa antivirusprograms funktionalitet.
Om du vill kontrollera statusen för realtidsskyddet utan att använda ESET Security Management Center, ansluter
du till klientdatorn via fjärrstyrning med Terminal och skickar följande kommando:
/Applications/.esets/Contents/MacOS/esets_daemon --status
Status för realtidsskannern visas antingen som RTPStatus=Enabled eller RTPStatus=Disabled.
Utgången för terminal bash inkluderar följande statusar:

14
• versionen av ESET Endpoint Security for macOS har installerats på klientdatorn
• detekteringsmotorns datum och version
• sökväg för att uppdatera server
OBS! Användning av Terminal rekommenderas endast för avancerade användare.
Vad gör jag om realtidsskyddet inte fungerar?
I detta kapitel beskrivs problemsituationer som kan uppstå när realtidsskyddet används och hur de felsöks.
Realtidsskyddet har inaktiverats
Om en användare inaktiverat realtidsskyddet av misstag måste det aktiveras på nytt. Återaktivera Realtidsskydd
från huvudmenyn genom att klicka på Inställningar > Dator och ställ in Skydd av filsystemet i realtid till
AKTIVERAT. Det går även att aktivera skydd av filsystemet i realtid i fönstret Avancerade inställningar under
Realtidsskydd genom att välja Aktivera skydd av filsystemet i realtid.
Realtidsskyddet identifierar och rensar inte infiltreringar
Kontrollera att inga andra antivirusprogram är installerade på datorn. Om två realtidsskydd är aktiverade samtidigt
kan de hamna i konflikt med varandra. Vi rekommenderar att avinstallera alla andra antivirusprogram på datorn.
Realtidsskyddet startar inte
Om realtidsskyddet inte startar vid systemstart kan det bero på konflikter med andra program. Kontakta ESET:s
kundtjänst om problemet uppstår.
Genomsökning av datorn
Om du misstänker att datorn är infekterad (den uppför sig onormalt), kör en Smart genomsökning och identifiera
eventuella infiltreringar. För maximalt skydd är det viktigt att genomsökningar av datorn inte endast utförs vid
misstänkt infektion, utan att de utförs regelbundet som en del av rutinåtgärder för säkerhet. Regelbunden
genomsökning kan identifiera infiltrationer som inte identifierades av realtidsskannern när de sparades på disken.
Detta kan inträffa om realtidsskannern var inaktiverad vid infektionstillfället eller om modulerna inte är
uppdaterade.

15
Vi rekommenderar att utföra en genomsökning av datorn på begäran minst en eller två gånger i månaden. Det går
att konfigurera genomsökning som en schemalagd aktivitet i Verktyg > Schemaläggaren.
Det går även att dra och släppa valda filer och mappar från skrivbordet eller fönstret Finder till huvudskärmen för
ESET Endpoint Security for macOS, dockningssymbolen, menyfältssymbolen (överst på skärmen) eller
programsymbolen (i mappen /Applications).
Typ av genomsökning
Det finns två typer av genomsökning av datorn på begäran. Smart genomsökning genomsöker datorn snabbt
utan ytterligare konfiguration av genomsökningsparametrarna. Anpassad genomsökning gör det möjligt att
välja en fördefinierad genomsökningsprofil och vissa genomsökningsobjekt.
Smart genomsökning
Smart genomsökning startar snabbt en genomsökning av datorn och rensar infekterade filer utan
användaråtgärder. Dess huvudsakliga fördel är enkel användning utan en detaljerad genomsökningskonfiguration.
Smart genomsökning kontrollerar alla filer i alla mappar och rensar eller tar bort identifierade infiltrationer.
Rensningsnivån är automatiskt inställd på standardvärdet. Se Rensning om du vill ha mer information om olika
typer av rensning.
Anpassad genomsökning
Anpassad genomsökning gör det möjligt att ange genomsökningsparametrar som t.ex. genomsökningsobjekt
och genomsökningsmetoder. Fördelen med att köra en anpassad genomsökning är möjligheten att konfigurera
genomsökningsparametrarna i detalj. Det går att spara olika konfigurationer som användardefinierade
genomsökningsprofiler som kan vara användbara om genomsökning upprepas med samma parametrar.

16
Välj genomsökningsobjekt genom att välja Genomsökning av datorn > Anpassad genomsökning och sedan
välja specifika Genomsökningsobjekt i trädet. Ett genomsökningsobjekt går att ange mer exakt genom att skriva
in sökvägen till mappen eller filerna som ska inkluderas. Är du endast intresserad av att söka igenom systemet
utan ytterligare rensningsåtgärder väljer du Genomsök utan rensning. Det går dessutom att ange en av tre
rensningsnivåer genom att klicka på Inställningar... > Rensning.
Anpassad genomsökning
Genomsökning av datorn med anpassad genomsökning rekommenderas endast för avancerade
användare med tidigare erfarenhet av antivirusprogram.
Genomsökningsobjekt
Genomsökningsobjektens trädstruktur gör det möjligt att välja filer och mappar som genomsöks efter virus. Det
går även att välja mappar enligt profilinställningarna.
Ett genomsökningsobjekt går att definiera mer exakt genom att skriva in sökvägen till mappen eller filerna som
ska inkluderas. Markera målobjekt i trädstrukturen som visar alla tillgängliga mappar på datorn genom att markera
kryssrutan för en viss fil eller mapp.
Genomsökningsprofiler
Det går att spara genomsökningsinställningarna för framtida genomsökning. Vi rekommenderar att skapar en profil
(med olika genomsökningsobjekt, genomsökningsmetoder och andra parametrar) för varje regelbunden
genomsökning.
Skapa en ny profil från huvudmenyn genom att klicka på Inställningar > Ange programinställningar... (eller
tryck på cmd+, > Genomsökning av datorn och klicka på Redigera... intill listan med aktuella profiler.
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
ESET Endpoint Security for macOS 6.9 Bruksanvisning
- Typ
- Bruksanvisning
Relaterade papper
-
ESET Endpoint Security for macOS 6.1X Bruksanvisning
-
ESET Endpoint Antivirus for macOS 6.11 Bruksanvisning
-
ESET Endpoint Antivirus for macOS 7 Bruksanvisning
-
ESET Cyber Security for macOS Snabbstartsguide
-
ESET Cyber Security for macOS 6 Bruksanvisning
-
ESET Cyber Security Pro for macOS 6 Bruksanvisning
-
ESET Endpoint Security for macOS Användarguide
-
ESET Endpoint Antivirus for macOS Användarguide
-
ESET ENDPOINT SECURITY 8 Bruksanvisning
-
ESET Endpoint Antivirus for Windows 8 Bruksanvisning


























































