
Copyright ©2018 ESET, spol. s r. o.
ESET Internet Security har utvecklats av ESET, spol. s r. o.
Besök www.eset.com för ytterligare information.
Alla rättigheter förbehålls. Ingen del av denna dokumentation får reproduceras, lagras i ett
hämtningssystem eller överföras i någon form, elektroniskt, mekaniskt, fotokopieras,
spelas in, skannas eller på annat sätt utan skriftligt tillstånd från författaren.
ESET, spol. s r. o. förbehåller sig rätten att ändra den beskrivna programvaran utan tidigare
meddelande.
Kundsupport i världen: www.eset.com/support
REV. 2018-10-01

Innehåll
.......................................................6ESET Internet Security1.
....................................................................................................7Nyheter i den här versionen1.1
....................................................................................................7Vilken produkt har jag?1.2
....................................................................................................8Systemkrav1.3
....................................................................................................8Skydd1.4
.......................................................10Installation2.
....................................................................................................10Live installer2.1
....................................................................................................11Offline-installation2.2
..............................................................................12Ange en licensnyckel
2.2.1
..............................................................................13Använda licenshanteraren
2.2.2
..............................................................................13Avancerade inställningar
2.2.3
....................................................................................................13Vanliga installationsproblem2.3
....................................................................................................13Produktaktivering2.4
....................................................................................................14Ange licensnyckel2.5
....................................................................................................14Uppgradering till en nyare version2.6
....................................................................................................15
Första genomsökningen efter
installation
2.7
.......................................................16Nybörjarguide3.
....................................................................................................16Programmets huvudfönster3.1
....................................................................................................18Uppdateringar3.2
....................................................................................................19Inställning av tillförlitliga platser3.3
....................................................................................................20Stöldskydd3.4
....................................................................................................21Verktyg för barnlåskontroll3.5
.......................................................22Arbeta med ESET Internet Security4.
....................................................................................................24Datorskydd4.1
..............................................................................25Detekteringsmotor
4.1.1
..................................................................................26Skydd av filsystemet i realtid
4.1.1.1
........................................................................27Ytterligare ThreatSense-parametrar
4.1.1.1.1
........................................................................27Rensningsnivåer
4.1.1.1.2
........................................................................28Ändring av konfiguration för realtidsskydd
4.1.1.1.3
........................................................................28Kontroll av realtidsskyddet
4.1.1.1.4
........................................................................28Vad gör jag om realtidsskyddet inte fungerar?
4.1.1.1.5
..................................................................................28Genomsökning av datorn
4.1.1.2
........................................................................29Starta anpassad genomsökning
4.1.1.2.1
........................................................................31Genomsökningsförlopp
4.1.1.2.2
........................................................................32Genomsökningsprofiler
4.1.1.2.3
........................................................................32Logg för genomsökning av datorn
4.1.1.2.4
..................................................................................32Genomsökning vid inaktivitet
4.1.1.3
..................................................................................33Startskanner
4.1.1.4
........................................................................33Kontroll av filer som startas automatiskt
4.1.1.4.1
..................................................................................33Exkluderade objekt
4.1.1.5
..................................................................................35ThreatSense-parametrar
4.1.1.6
........................................................................39Rensning
4.1.1.6.1
........................................................................39Filändelser som är undantagna från genomsökning
4.1.1.6.2
..................................................................................40En infiltration identifieras
4.1.1.7
..................................................................................42Dokumentskydd
4.1.1.8
..............................................................................42Flyttbara medier
4.1.2
..............................................................................43Enhetskontroll
4.1.3
..................................................................................44Regelredigerare för enhetskontroll
4.1.3.1
..................................................................................45Lägga till regler för enhetskontroll
4.1.3.2
..................................................................................46Regelredigerare för webbkameraskydd
4.1.3.3
..............................................................................46Självskyddet HIPS (Host Intrusion Prevention System)
4.1.4
..................................................................................48Avancerade inställningar
4.1.4.1
..................................................................................49HIPS interaktivt fönster
4.1.4.2
..................................................................................50Ett potentellt ransomware-beteende upptäcktes
4.1.4.3
..............................................................................50Spelläge
4.1.5
....................................................................................................51Internetskydd4.2
..............................................................................52Webbåtkomstskydd
4.2.1
..................................................................................52Grundläggande
4.2.1.1
..................................................................................53Webbprotokoll
4.2.1.2
..................................................................................53URL-adressbehandling
4.2.1.3
..............................................................................54Skydd av e-postklient
4.2.2
..................................................................................54E-postklienter
4.2.2.1
..................................................................................55E-postprotokoll
4.2.2.2
..................................................................................56Varningar och meddelanden
4.2.2.3
..................................................................................57Integrering med e-postklienter
4.2.2.4
........................................................................57Konfigurering av skydd för e-postklient
4.2.2.4.1
..................................................................................57POP3-, POP3S-filter
4.2.2.5
..................................................................................58Antispammodul
4.2.2.6
..............................................................................59Protokollfiltrering
4.2.3
..................................................................................59Webbläsare och e-postklienter
4.2.3.1
..................................................................................60Undantagna program
4.2.3.2
..................................................................................61Undantagna IP-adresser
4.2.3.3
........................................................................61Lägg till IPv4-adress
4.2.3.3.1
........................................................................61Lägg till IPv6-adress
4.2.3.3.2
..................................................................................62SSL/TLS
4.2.3.4
........................................................................63Certifikat
4.2.3.4.1
........................................................................63Krypterad nätverkstrafik
4.2.3.4.1.1
........................................................................63Lista över kända certifikat
4.2.3.4.2
........................................................................64Lista över SSL/TLS-filtrerade program
4.2.3.4.3
..............................................................................64Skydd mot nätfiske
4.2.4
....................................................................................................65Nätverksskydd4.3
..............................................................................67Brandvägg
4.3.1
..................................................................................68Inställningar för inlärningsläge
4.3.1.1
..................................................................................69Skydd mot nätverksattacker
4.3.1.2
..............................................................................69Brandväggsprofiler
4.3.2
..................................................................................70Profiler som tilldelats till nätverkskort
4.3.2.1
..............................................................................70Konfigurera och använda regler
4.3.3
..................................................................................71Regler för brandvägg
4.3.3.1
..................................................................................72Arbeta med regler
4.3.3.2
..............................................................................72Konfigurera zoner
4.3.4
..............................................................................73Kända nätverk
4.3.5
..................................................................................73Redigerare för kända nätverk
4.3.5.1
..................................................................................76Nätverksautentisering – serverkonfiguration
4.3.5.2
..............................................................................76Loggning
4.3.6
..............................................................................76Etablera en anslutning - identifiering
4.3.7
..............................................................................77Lösa problem med ESET Personlig brandvägg
4.3.8
..................................................................................77Felsökningsguide
4.3.8.1
..................................................................................77Logga och skapa regler eller undantag från logg
4.3.8.2

........................................................................77Skapa regel från logg
4.3.8.2.1
..................................................................................78Skapa undantag från brandväggsmeddelanden
4.3.8.3
..................................................................................78Avancerad PCAP-loggning
4.3.8.4
..................................................................................78Lösa problem med protokollfiltrering
4.3.8.5
....................................................................................................79Säkerhetsverktyg4.4
..............................................................................79Föräldrakontroll
4.4.1
..................................................................................81Kategorier
4.4.1.1
..................................................................................82Webbplatsundantag
4.4.1.2
....................................................................................................83Uppdatera programmet4.5
..............................................................................86Uppdateringsinställningar
4.5.1
..................................................................................88Avancerade uppdateringsinställningar
4.5.1.1
........................................................................88Uppdateringsläge
4.5.1.1.1
........................................................................88Anslutningsalternativ
4.5.1.1.2
..............................................................................89Ångra uppdatering
4.5.2
..............................................................................90Skapa uppdateringsaktiviteter
4.5.3
....................................................................................................91Verktyg4.6
..............................................................................91Övervakning av uppkopplat hem
4.6.1
..................................................................................92Nätverksenhet
4.6.1.1
..............................................................................93Webbkameraskydd
4.6.2
..............................................................................93Verktyg i ESET Internet Security
4.6.3
..................................................................................94Loggfiler
4.6.3.1
........................................................................95Loggfiler
4.6.3.1.1
..................................................................................96Processer som körs
4.6.3.2
..................................................................................98Säkerhetsrapport
4.6.3.3
..................................................................................99Se aktivitet
4.6.3.4
..................................................................................100Nätverksanslutningar
4.6.3.5
..................................................................................101ESET SysInspector
4.6.3.6
..................................................................................101Schemaläggare
4.6.3.7
..................................................................................103Systemrensare
4.6.3.8
..................................................................................103ESET SysRescue
4.6.3.9
..................................................................................104Molnbaserat skydd
4.6.3.10
........................................................................105Misstänkta filer
4.6.3.10.1
..................................................................................106Karantän
4.6.3.11
..................................................................................107Proxyserver
4.6.3.12
..................................................................................108Meddela via e-post
4.6.3.13
........................................................................109Meddelandeformat
4.6.3.13.1
..................................................................................109Välj prov för analys
4.6.3.14
..................................................................................110Microsoft Windows®-uppdatering
4.6.3.15
..................................................................................110ESET CMD
4.6.3.16
....................................................................................................112Användargränssnitt4.7
..............................................................................112Element i användargränssnitt
4.7.1
..............................................................................113Varningar och meddelanden
4.7.2
..................................................................................114Avancerade inställningar
4.7.2.1
..............................................................................115Inställningar för åtkomst
4.7.3
..............................................................................116Programmeny
4.7.4
.......................................................118Avancerade användare5.
....................................................................................................118Profiler5.1
....................................................................................................118Tangentbordsgenvägar5.2
....................................................................................................119Diagnostik5.3
....................................................................................................120Importera och exportera inställningar5.4
....................................................................................................120ESET SysInspector5.5
..............................................................................120Introduktion till ESET SysInspector
5.5.1
..................................................................................121Starta ESET SysInspector
5.5.1.1
..............................................................................121Användargränssnitt och programanvändning
5.5.2
..................................................................................121Programkontroller
5.5.2.1
..................................................................................123Navigera i ESET SysInspector
5.5.2.2
........................................................................124Tangentbordsgenvägar
5.5.2.2.1
..................................................................................125Jämför
5.5.2.3
..............................................................................126Kommandoradsparametrar
5.5.3
..............................................................................127Tjänsteskript
5.5.4
..................................................................................127Generera tjänsteskript
5.5.4.1
..................................................................................127Tjänsteskriptets struktur
5.5.4.2
..................................................................................130Köra tjänsteskript
5.5.4.3
..............................................................................131FAQ
5.5.5
....................................................................................................132Kommandorad5.6
.......................................................134Ordlista6.
....................................................................................................134Typer av infiltreringar6.1
..............................................................................134Virus
6.1.1
..............................................................................134Maskar
6.1.2
..............................................................................134Trojaner
6.1.3
..............................................................................135Rootkit
6.1.4
..............................................................................135Reklamprogram
6.1.5
..............................................................................135Spionprogram
6.1.6
..............................................................................136Komprimeringsprogram
6.1.7
..............................................................................136Potentiellt farliga program
6.1.8
..............................................................................136Potentiellt oönskade program
6.1.9
..............................................................................139Botnet
6.1.10
....................................................................................................139Typer av fjärrangrepp6.2
..............................................................................139DOS-attacker
6.2.1
..............................................................................139DNS-förgiftning
6.2.2
..............................................................................139Maskattacker
6.2.3
..............................................................................139Portgenomsökning
6.2.4
..............................................................................140TCP-desynkronisering
6.2.5
..............................................................................140SMB-relä
6.2.6
..............................................................................140ICMP-attacker
6.2.7
....................................................................................................141ESET Technology6.3
..............................................................................141Kryphålsblockering
6.3.1
..............................................................................141Avancerad minnesskanner
6.3.2
..............................................................................141Skydd mot nätverksattacker
6.3.3
..............................................................................141ESET LiveGrid®
6.3.4
..............................................................................142Botnätsskydd
6.3.5
..............................................................................142Java-kryphålsblockering
6.3.6
..............................................................................142Bank- och betalningsskydd
6.3.7
..............................................................................143Skydd mot skriptbaserade attacker
6.3.8
..............................................................................143Sköld mot ransomware
6.3.9
..............................................................................143UEFI-skanner
6.3.10
....................................................................................................144E-post6.4
..............................................................................144Annonser
6.4.1
..............................................................................144Bluffar
6.4.2
..............................................................................145Nätfiske
6.4.3
..............................................................................145Känna igen spambedrägerier
6.4.4

Innehåll
..................................................................................145Regler
6.4.4.1
..................................................................................146Vitlista
6.4.4.2
..................................................................................146Svartlista
6.4.4.3
..................................................................................146Undantagslista
6.4.4.4
..................................................................................146Kontroll på serversidan
6.4.4.5
.......................................................147Vanliga frågor7.
....................................................................................................147Uppdatera ESET Internet Security7.1
....................................................................................................147Ta bort ett virus från datorn7.2
....................................................................................................148
Tillåta kommunikation för ett visst
program
7.3
....................................................................................................148Aktivera Föräldrakontroll för ett konto7.4
....................................................................................................149Skapa en ny aktivitet i Schemaläggare7.5
....................................................................................................150
Schemalägga en veckovis genomsökning
av datorn
7.6
....................................................................................................150Låsa upp avancerade inställningar7.7

6
1. ESET Internet Security
ESET Internet Security representerar ett nytt förhållningssätt till integrerad datasäkerhet. Resultatet är ett
intelligent system som är oupphörligen vaksamt mot attacker och skadlig programvara som kan utgöra en fara för
din dator.
ESET Internet Security är en komplett säkerhetslösning som kombinerar maximalt skydd och minimal
systembelastning. Vår avancerade teknik som använder artificiell intelligens för att förhindra infiltration av virus,
spionprogram, trojaner, maskar, reklamprogram, rootkits och andra hot utan att minska systemets prestanda eller
störa din dator.
Funktioner och fördelar
Omformat användargränssnitt
Användargränssnittet i den här versionen har omformats avsevärt och
förenklats baserat på resultat från testning av användarvänlighet. All GUI-
text och alla meddelanden har granskats noga och gränssnittet har nu stöd
för språk som skrivs från höger till vänster, som hebreiska och arabiska.
Onlinehjälpen är nu integrerad i ESET Internet Security och har
supportinnehåll som uppdateras dynamiskt.
Skydd mot virus och
spionprogram
Identifierar och rensar proaktivt kända och okända virus, maskar, trojaner
och rootkits. Avancerad heuristik varnar även för inte tidigare känd
skadlig kod och skyddar dig mot okända hot och neutraliserar dem innan
de hinner göra skada. Webbåtkomstskydd och Skydd mot nätfiske
övervakar kommunikation mellan webbläsare och fjärrservrar (inklusive
SSL). Skydd av e-postklient kontrollerar e-postkommunikation genom
POP3(S)- och IMAP(S)-protokollen.
Regelbundna uppdateringar
Regelbunden uppdatering av detekteringsmotorn (som tidigare kallades
virussignaturdatabas) och programmodulerna är det bästa sättet att
säkerställa maximal skyddsnivå för datorn.
ESET LiveGrid®
(molngenererat rykte)
Det går att kontrollera ryktet för processer och filer som körs direkt i ESET
Internet Security.
Enhetskontroll
Söker automatiskt igenom USB-flashenheter, minneskort och CD/DVD.
Blockerar flyttbara medier baserat på mediatyp, tillverkare, storlek och
andra attribut.
HIPS-funktion
Det går att anpassa systemets beteende i större detalj. Ange regler för
systemregistret, aktiva processer och program och finjustera
säkerhetsinställningarna.
Spelläge
Skjuter upp alla popup-fönster, uppdateringar och andra systemintensiva
aktiviteter för att spara systemresurser för spel och andra aktiviteter i
helskärmsläge.
En licens krävs för att funktionerna i ESET Internet Security ska fungera. Vi rekommenderar att du förnyar din licens
flera veckor innan licensens för ESET Internet Security upphör att gälla.

7
1.1 Nyheter i den här versionen
Den nya versionen ESET Internet Security har följande förbättringar:
Loggning med ett klick – det går att skapa avancerade loggar med endast ett klick.
UEFI-skanner (Unified Extensible Firmware Interface) – ger utökat skydd mot skadlig kod genom att detektera och
avlägsna hot som kan starta redan under uppstart av operativsystemet. För mer information, klicka här.
Höga prestanda och låg systempåverkan – den här versionen är utformad för effektivt utnyttjande av systemets
resurser, så att du kan använda datorns prestanda fullt ut samtidigt som du är skyddad mot nya typer av hot.
Omorganisering av avancerade inställningar – inställningarna för ESET LiveGrid® har flyttats till avsnittet
Detekteringsmotor, avancerad loggning för spamskydd har flyttats till avsnittet Diagnostik och så vidare.
Bättre stöd för skärmläsare – ESET Internet Security har stöd för de flesta populära skärmläsare (JAWS, NVDA,
Narrator).
Genomsökning med dra och släpp – du kan genomsöka en fil eller mapp manuellt genom att helt enkelt flytta
filen eller mappen till det markerade området.
ESET Internet Security installeras nu med ett minimum av moduler, så att installationen är mindre krävande och
går snabbare. Modulerna börjar sedan hämtas när produkten har installerats och aktiverats.
ESET Internet Security informerar dig när du ansluter till ett oskyddat trådlöst nätverk eller ett nätverk med svagt
skydd.
Ytterligare information om de nya funktionerna i ESET Internet Security finns i följande artikel i ESET:s kunskapsbas:
Nyheter i den här versionen av ESET:s hemprodukter
1.2 Vilken produkt har jag?
ESET erbjuder flera lager av säkerhet med nya produkter – från en kraftfull och snabb antiviruslösning till en
heltäckande säkerhetslösning med minimal systempåverkan:
ESET NOD32 Antivirus
ESET Internet Security
ESET Smart Security Premium
Om du vill se vilken produkt du har installerad öppnar du programmets huvudfönster (se artikeln i kunskapsbasen),
så visas produktens namn överst i fönstret (huvudet).
I tabellen nedan visas vilka funktioner respektive produkt har.
ESET NOD32 Antivirus
ESET Internet Security
ESET Smart Security
Premium
Antivirus
Skydd mot spionprogram
Kryphålsblockering
Skydd mot skriptbaserade
attacker
Skydd mot nätfiske
Webbåtkomstskydd
HIPS (inklusive Skydd mot
ransomware)
Antispam

8
Brandvägg
Övervakning av uppkopplat hem
Webbkameraskydd
Skydd mot nätverksattacker
Botnätsskydd
Bank- och betalningsskydd
Föräldrakontroll
Stöldskydd
ESET Password Manager
ESET Secure Data
OBS!
Vissa av produkterna ovan kanske inte är tillgängliga på ditt språk eller i din region.
1.3 Systemkrav
Om ESET Internet Security ska fungera optimalt ska systemet uppfylla följande krav på maskin- och programvara:
Processorer som stöds
Intel® eller AMD x86-x64
Operativsystem som stöds
Microsoft® Windows® 10
Microsoft® Windows® 8.1
Microsoft® Windows® 8
Microsoft® Windows® 7
Microsoft® Windows® Vista
Microsoft® Windows® Home Server 2011 64-bitars
OBS!
ESET Stöldskydd har inte stöd för Microsoft Windows Home Servers.
1.4 Skydd
När du använder datorn, särskilt när du surfar på Internet, bör du komma ihåg att inget antivirussystem i världen
fullständigt kan eliminera risken för infiltreringar och attacker. För att uppnå maximalt skydd och bekvämlighet är
det viktigt att använda antiviruslösningen på ett korrekt sätt och följa några praktiska regler:
Uppdatera regelbundet
Enligt statistik från ThreatSense skapas tusentals nya unika infiltreringar varje dag. De kan ta sig förbi befintliga
säkerhetsåtgärder och berika sina författare, allt på andra användares bekostnad. Specialisterna i ESET:s
forskningslabb analyserar dagligen dessa hot. De utvecklar och släpper uppdateringar så att användarnas skyddsnivå
hela tiden höjs. För att säkerställa att uppdateringarna för maximal effekt är det viktigt att uppdateringarna är
korrekt inställda på systemet. Ytterligare information om konfigurering av uppdateringar finns i kapitlet
Uppdateringsinställningar.
Hämta säkerhetskorrigeringsfiler
Författarna till skadlig programvara utnyttjar ofta olika sårbarheter i systemet så att spridningen av skadlig kod blir
effektivare. Med detta i åtanke letar programvaruföretag noga efter nya sårbarheter i sina program så att de kan
släppa säkerhetsuppdateringar som regelbundet eliminerar potentiella hot så snart en sårbarhet har påvisats. Det är

9
viktigt att hämta dessa säkerhetsuppdateringar så snart de släpps. Microsoft Windows och webbläsare som Internet
Explorer är två exempel på program för vilka säkerhetsuppdateringar släpps regelbundet.
Säkerhetskopiera viktiga data
Författare till skadlig programvara bryr sig vanligtvis inte om användarnas behov och skadliga program leder ofta till
att operativsystemet helt slutar fungera och att viktiga data går förlorade. Det är viktigt att regelbundet
säkerhetskopiera viktiga och känsliga data till en extern källa som en DVD-skiva eller en extern hårddisk. Detta gör
det mycket snabbare och enklare att återställa data om datorn eller systemet slutar fungera.
Genomsök regelbundet datorn efter virus
Identifiering av fler kända och okända virus, maskar, trojaner och rootkit hanteras av skyddsmodulen för
realtidsövervakning av filsystemet. Detta innebär att varje gång du öppnar en fil, genomsöks den efter skadlig kod.
Vi rekommenderar att du kör en fullständig genomsökning av datorn åtminstone en gång per månad, eftersom
skadlig kod ändras och detekteringsmotorn uppdateras varje dag.
Följ grundläggande säkerhetsregler
Detta är den viktigaste och mest effektiva regeln av alla – var alltid försiktig! Idag kräver många infiltreringar att
användaren reagerar innan de körs och sprids. Om du är försiktig innan du öppnar nya filer sparar du mycket tid och
kraft som annars skulle gå åt till att rensa bort infiltreringar. Här är några praktiska riktlinjer:
Besök inte misstänkta webbplatser med flera popup-fönster och blinkande annonser.
Var försiktig när du installerar gratisprogram, codec-paket o.s.v. Använd endast säkra program och besök
endast säkra webbplatser.
Var försiktig när du öppnar bifogade filer i e-postmeddelanden, särskilt om meddelandet har skickats till
många mottagare eller kommer från en okänd avsändare.
Använd inte ett administratörskonto för dagligt arbete med datorn.

10
2. Installation
Det finns flera sätt att installera ESET Internet Security på din dator. Installationssätten kan variera beroende på land
och distributionssätt:
Live installer kan hämtas från ESET-webbplatsen. Installationspaketet är gemensamt för alla språk (välj önskat
språk). Live installer är en liten fil och ytterligare filer som krävs för att installera ESET Internet Security hämtas
automatiskt.
Offline-installation – den här typen av installation används när du installerar från en produkt-CD/-DVD. Den
använder en .exe-fil som är större än Live installer-filen och inte kräver en Internet-anslutning eller ytterligare
filer för installationens slutförande.
VIKTIGT!
Kontrollera att inga andra antivirusprogram är installerade på datorn innan du installerar ESET Internet Security.
Om två eller fler antiviruslösningar är installera på en dator kan de komma i konflikt med varandra. Det
rekommenderas att du avinstallerar alla andra antivirusprogram på datorn. Se vår artikel i ESET kunskapsbas för
en lista med avinstallationsverktyg för vanliga antivirusprogram (finns på engelska och flera andra språk).
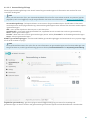
2.1 Live installer
När du har hämatat Live installer-installationspaketet dubbelklickar du på installationsfilen och följer
instruktionerna steg för steg i installationsfönstret.
VIKTIGT!
För den här typen av installation måste du anslutas till Internet.
Välj önskat språk i listrutan och klicka på Fortsätt. Låt det gå några ögonblick för installationsfilerna att laddas ner.
Efter att du har godkänt Licensavtalet för slutanvändare blir du ombedd att konfigurera ESET LiveGrid® och
detektering av potentiellt oönskade program. ESET LiveGrid® bidrar till att säkerställa att ESET alltid har den senaste
informationen om hot för att skydda kunderna. Systemet tillåter att nyupptäckta hot skickas till ESET:s
forskningslabb där de analyseras, bearbetas och läggs till i detekteringsmotorn.
Enligt standard är Aktivera ESET LiveGrid®-feedbacksystemet (rekommenderas) markerat, vilket aktiverar den här
funktionen.

11
Nästa steg i installationsprocessen är konfiguration av Detektering av potentiellt oönskade program. Potentiellt
oönskade program är inte nödvändigtvis skadliga, men de kan ändå påverka operativsystemets prestanda negativt.
Se kapitlet Potentiellt oönskade program för ytterligare information.
Klicka på Installera för att starta installationsprocessen. Detta kan ta en stund. Avsluta produktinstallationen och
starta aktiveringen genom att klicka på Klar.
OBS!
När produkten har installerats och aktiverats börjar modulerna hämtas. Skyddet initieras och det är inte säkert att
alla funktioner fungerar förrän hämtningen är klar.
OBS!
Om du har en licens som du kan installera andra versioner av en produkt med, så kan du välja produkt efter
önskemål. Klicka här om du vill läsa mer om funktionerna i de olika produkterna.
2.2 Offline-installation
När du har startat offlineinstallationen (.exe) tar installationsguiden dig igenom installationen.
Välj önskat språk i listrutan och klicka på Installera.
När du har godkänt licensavtalet för slutanvändare ombeds du att ange en licensnyckel eller använda
licenshanteraren.
Om du inte har en licens än väljer du Gratis utvärdering om du vill testa ESET-produkten under en begränsad
tidsperiod eller väljer Köp licens. Alternativt kan du välja Hoppa över aktivering för att fortsätta med installationen
utan aktivering. Du ombeds då att ange en licensnyckel senare.

12
2.2.1 Ange en licensnyckel
Installationsguiden väljer produkt att installera utifrån licensnyckeln och visar produktnamnet under installationen.
Om du vill visa en lista över produkter som kan aktiveras med licensen klickar du på Byt produkt. För mer
information om funktionerna i varje produkt klickar du här.
Klicka på Fortsätt och välj önskade inställningar förESET LiveGrid® och detektering av potentiellt oönskade program.
ESET LiveGrid® bidrar till att säkerställa att ESET alltid har den senaste informationen om hot för att skydda
kunderna. Systemet tillåter att nyupptäckta hot skickas till ESET:s forskningslabb där de analyseras, bearbetas och
läggs till i detekteringsmotorn. Potentiellt oönskade program är inte nödvändigtvis skadliga, men de kan ändå
påverka operativsystemets prestanda negativt. Se kapitlet Potentiellt oönskade program för ytterligare
information.
Klicka på Installera för att starta installationsprocessen. Detta kan ta en stund. Avsluta produktinstallationen och
starta aktiveringen genom att klicka på Klar.
OBS!
När produkten har installerats och aktiverats börjar modulerna hämtas. Skyddet initieras och det är inte säkert att
alla funktioner fungerar förrän hämtningen är klar.
OBS!
Om du har en licens som du kan installera olika produkter med, så kan du välja produkt efter önskemål. Klicka här
om du vill läsa mer om funktionerna i de olika produkterna.
För mer instruktioner om installationssteg, ESET LiveGrid® och Detektering av potentiellt oönskade program följer
du anvisningarna i avsnittet Live installer.

13
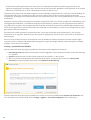
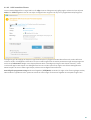
2.2.2 Använda licenshanteraren
När du har valt Använd licenshanteraren ombeds du att ange inloggningsuppgifterna till my.eset.com i ett nytt
fönster. Ange uppgifterna och klicka på Logga in om du vill använda en licens i licenshanteraren. Välj en licens för
aktivering och klicka på Fortsätt, så aktiveras ESET Internet Security.
OBS!
Om du inte har ett konto på my.eset.com än registrerar du ett genom att klicka på knappen Skapa konto.
OBS!
Om du har glömt lösenordet klickar du på Jag har glömt lösenordet och följer stegen på webbsidan du
omdirigeras till.
Med ESET-licenshanteraren kan du hantera alla dina ESET-licenser. Du kan smidigt förnya, uppgradera eller utöka din
licens och visa viktig licensinformation. Ange först licensnyckeln. Sedan visas produkt, associerad enhet, antal
tillgängliga platser och utgångsdatum. Det går att inaktivera eller byta namn på specifika enheter. När du klickar på
Förnya omdirigeras du till webbutiken där du kan bekräfta köpet och köpa förnyelsen.
Om du vill uppgradera din licens (till exempel från ESET NOD32 Antivirus till ESET Smart Security Premium) eller vill
installera en ESET-säkerhetsprodukt i en annan enhet omdirigeras du till webbutiken så att köpet kan slutföras.
I ESET-licenshanteraren kan du även lägga till olika licenser, hämta produkter till dina enheter.
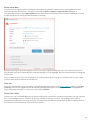
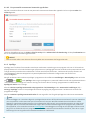
2.2.3 Avancerade inställningar
När du har valt Ändra installationsmapp ombeds du välja plats för installationen. Som standar installeras
programmet i följande katalog:
C:\Program Files\ESET\ESET Internet Security\
Klicka på Bläddra för att byta plats (rekommenderas inte).
Slutför nästa installationssteg, ESET LiveGrid® och Detektering av potentiellt oönskade program genom att följa
anvisningarna i avsnittet Live installer (se Live installer).
Klicka på Fortsätt och sedan Installera för att slutföra installationen.
2.3 Vanliga installationsproblem
Om det uppstår problem under installationen, se vår lista med vanliga installationsfel och lösningar på dem för att
hitta en lösning på problemet.
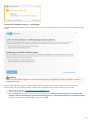
2.4 Produktaktivering
När installationen är slutförd ombeds du aktivera produkten.
Det går att aktivera produkten på flera sätt. Tillgänglighet för ett visst aktiveringssätt i aktiveringsfönstret kan bero
på land och distributionssätt (CD/DVD, ESET webbsida osv.):
Köpte du en förpackad återförsäljarversion av produkten, så aktiverar du den med en Licensnyckel.
Licensnyckeln finns normalt inne i eller på baksidan av produktens förpackning. Licensnyckeln måste anges för
att slutföra aktiveringen. Licensnyckel – en unik sträng i formatet XXXX-XXXX-XXXX-XXXX-XXXX eller XXXX-
XXXXXXXX som används för att identifiera licensägaren och aktivera licensen.
När du har valt Använd licenshanteraren ombeds du att ange inloggningsuppgifterna till my.eset.com i ett nytt
fönster.
Om du vill prova ESET Internet Security innan du köper det, välj Gratis utvärdering. Ange din e-postadress och
ditt land för att aktivera ESET Internet Security under en begränsad tid. Provlicensen skickas till dig per e-post.
Det går endast att aktivera en provlicens per kund.
Har du ingen licens och vill köpa en, klicka på Köp licens. Detta för dig till ESET:s lokala återförsäljares

14
webbplats.
2.5 Ange licensnyckel
Automatiska uppdateringar är viktiga för din säkerhet. ESET Internet Security tar endast emot uppdateringar när det
aktiverats med din Licensnyckel.
Om licensnyckeln inte anges efter installationen aktiveras inte produkten. Du kan ändra licensen i programmets
huvudfönster. Om du vill göra det klickar du på Hjälp och support > Aktivera licens och anger licensuppgifterna du
fick till din ESET-säkerhetsprodukt i fönstret Produktaktivering.
När du anger din Licensnyckel är det viktigt att den anges exakt som den är skriven:
Licensnyckeln är en unik sträng i formatet XXXX-XXXX-XXXX-XXXX-XXXX som används för att identifiera
licensägaren och aktivera licensen.
Vi rekommenderar att kopiera och klistra in licensnyckeln från registreringsmeddelandet för noggrannhet.
2.6 Uppgradering till en nyare version
Nya versioner av ESET Internet Security kommer ut för att genomföra förbättringar eller lösa problem som inte går
att åtgärda med automatiska uppdateringar av programmodulerna. Det går att uppdatera till en nyare version på
flera sätt:
1. Automatiskt genom programuppdatering.
Eftersom programuppdateringen distribueras till alla användare och kan påverka vissa systemkonfigurationer
släpps de efter en lång testperiod för att säkerställa att de fungerar med alla tänkbara systemkonfigurationer.
Använd en av metoderna nedan om du måste uppgradera till en nyare version omedelbart när den kommer ut.
2. Manuellt i programmets huvudfönster genom att klicka på Leta efter uppdateringar i avsnittet Uppdatera.
3. Manuellt genom att hämta och installera en nyare version över den föregående.

15
2.7 Första genomsökningen efter installation
När ESET Internet Security installerats startar en datorgenomsökning automatiskt efter den första uppdateringen för
att söka efter skadlig kod.
Det går också att starta en datorgenomsökning manuellt från programmets huvudfönster genom att klicka på
Genomsökning av datorn > Genomsök datorn. Mer information om datorgenomsökning finns i avsnittet
Genomsökning av datorn.

16
3. Nybörjarguide
Detta kapitel ger en inledande översikt över ESET Internet Security och grundinställningarna.
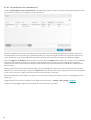
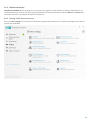
3.1 Programmets huvudfönster
ESET Internet Security huvudfönster är indelat i två huvuddelar. Det primära fönstret till höger visar information
som motsvarar alternativt som valts i huvudmenyn till vänster.
Här följer en beskrivning av alternativen på huvudmenyn:
Startfönster – ger information om skyddsstatus för ESET Internet Security.
Genomsökning av datorn – konfigurera och starta en genomsökning av datorn eller skapa en anpassad
genomsökning.
Uppdatering – visar information om uppdateringar av detekteringsmotorn.
Verktyg – ger åtkomst till loggfiler, skyddsstatistik, Övervaka aktivitet, processer som körs, nätverksanslutningar,
schemaläggaren, ESET SysInspector och ESET SysRescue.
Inställningar – välj detta alternativ för att justera säkerhetsnivån för Dator, Internet, Nätverksskydd och
Säkerhetsverktyg.
Hjälp och support – ger åtkomst till hjälpfiler, ESET:s kunskapsbas, ESET:s webbplats och länkar för att skicka
supportfrågor.
Skärmen Hem innehåller viktig information om datorns aktuella skyddsnivå. Statusfönstret visar ofta använda
funktioner i ESET Internet Security. Information om den senaste uppdateringen och programmets utgångsdatum
finns också här.
Den gröna ikonen och gröna statusen för Maximalt skydd visar att maximalt skydd garanteras.

17
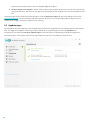
Vad gör jag om programmet inte fungerar?
Om en aktiv skyddsmodul fungerar korrekt är dess skyddsstatusikon grön. Ett rött utropstecken eller en orange
meddelandeikon indikerar att maximalt skydd inte är säkerställt. Ytterligare information om skyddsstatus för varje
modul, liksom föreslagna lösningar för att återställa fullständigt skydd, visas under Hem. Ändra status för enskilda
moduler genom att klicka på Inställningar och välja önskad modul.
Den röda ikonen och statusen Det går inte att garantera maximalt skydd indikerar allvarliga problem.
Det finns flera skäl till att denna status kan visas, som till exempel:
Produkten inte aktiverad – du kan aktivera ESET Internet Security från Hem genom att klicka på antingen
Aktivera produkt eller Köp nu under Skyddsstatus.
Detekteringsmotorn är inaktuell – detta fel visas efter flera misslyckade försök att uppdatera
detekteringsmotorn. Vi rekommenderar att kontrollera uppdateringsinställningarna. Den vanligaste
orsaken till detta fel är felaktigt angivna autentiseringsdata eller felaktigt konfigurerade
anslutningsinställningar.
Skydd mot virus och spionprogram inaktiverade – du kan aktivera skyddet mot virus och spionprogram
igen genom att klicka på Aktivera skydd mot virus och spionprogram.
ESET-brandväggen är inaktiverad – detta problem indikeras även med ett säkerhetsmeddelande intill
objektet Nätverk på skrivbordet. Det går att återaktivera nätverksskyddet genom att klicka på Aktivera
brandvägg.
Licensen har upphört – detta indikeras med en röd skyddsstatusikon. Programmet kan inte uppdateras när
licensen har gått ut. Följ anvisningarna i varningsfönstret för att förnya licensen.
Den orangea ikonen indikerar begränsat skydd. Det kan exempelvis vara problem med att uppdatera licensen
eller så kan licensens utgångsdatum närma sig.
Det finns flera skäl till att denna status kan visas, som till exempel:
Spelläge aktivt – att aktivera Spelläge är en potentiell säkerhetsrisk. Om funktionen aktiveras, så

18
inaktiveras alla popup-fönster och schemalagda åtgärder stoppas.
Licensen upphör snart att gälla – detta indikeras genom att skyddsstatusikonen och visar ett utropstecken
intill systemklockan. När licensen har gått ut kan programmet inte uppdatera och ikonen Skyddsstatus blir
röd.
Om det inte går att lösa problemet med förslagen, klicka på Hjälp och support för att visa hjälpfilerna eller sök i
ESET:s kunskapsbas. Om du fortfarande behöver hjälp kan du skicka in en supportfråga. ESET kundtjänst svarar
snabbt på dina frågor och hjälper dig att hitta en lösning.
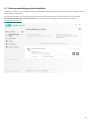
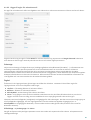
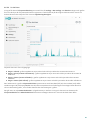
3.2 Uppdateringar
Att uppdatera detekteringsmotorn och programkomponenterna är avgörande för att skydda systemet mot skadlig
kod. Var noggrann vad gäller inställning och genomförande av uppdateringarna. Klicka på Uppdatera på
huvudmenyn och sedan på Leta efter uppdateringar för att söka efter en uppdatering av detekteringsmotorn.
Om licensnyckeln inte angavs under aktivering av ESET Internet Security ombeds du ange dem nu.

19
Fönstret Avancerade inställningar (klicka på Inställningar på huvudmenyn och klicka sedan på Avancerade
inställningar eller tryck på F5 på tangentbordet) innehåller ytterligare uppdateringsalternativ. Klicka på aktuell flik i
fönstret Uppdatering för att konfigurera avancerade uppdateringsalternativ som uppdateringsläge,
proxyserveråtkomst och LAN-anslutningar.
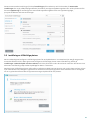
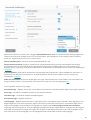
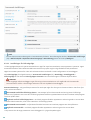
3.3 Inställning av tillförlitliga platser
Det är nödvändigt att konfigurera tillförlitliga platser för att skydda datorn i en nätverksmiljö. Det går att ge andra
användare åtkomst till din dator genom att konfigurera Tillförlitliga platser samt tillåta delning. Klicka på
Inställningar > Nätverksskydd > Anslutna nätverk och klicka på länken under det anslutna nätverket. Ett fönster visar
alternativ som låter dig välja önskat skyddsläge för datorn i nätverket.
Detektering av tillförlitliga platser utförs efter installation av ESET Internet Security och när din dator ansluter till ett
nytt nätverk. Det finns vanligtvis inget behov av att definiera Tillförlitliga platser. Som standard visas en dialogruta
när en ny plats identifierats där du uppmanas att ange skyddsnivå för den platsen.

20
VARNING!
Att felaktigt konfigurera platser som tillförlitliga kan innebära en säkerhetsrisk för datorn.
OBS!
Som standard får arbetsstationer på tillförlitliga platser åtkomst till delade filer och skrivare, inkommande RPC-
kommunikation aktiveras och delning av fjärrskrivbord blir tillgängligt.
För mer information om funktionen, se följande artikel i ESET kunskapsbas:
Ny nätverksanslutning upptäckt i ESET Smart Security
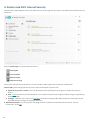
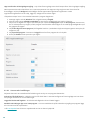
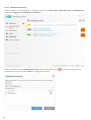
3.4 Stöldskydd
Skydda din dator i händelse av förlust eller stöld genom att välja bland följande alternativ att registrera datorn i ESET
Stöldskydd-systemet.
1. Klicka på Aktivera Stöldskydd efter aktiveringen för att aktivera ESET Stöldskydd-funktionerna för dator du nyss
registrerade.
2. Om du ser meddelandet ESET Stöldskydd är tillgänglig på Hemskärmen för ESET Internet Security, ska du beakta
att aktivera den här funktionen för datorn. Klicka på Aktivera ESET Stöldskydd för att registrera datorn med ESET
Stöldskydd.
3. Klicka på Inställningar > Säkerhetsverktyg i programmets huvudfönster. Klicka på bredvid ESET
Stöldskydd och följ anvisningarna i popup-fönstret..
OBS!
ESET Stöldskydd har inte stöd för Microsoft Windows Home Servers.
Ytterligare anvisningar om ESET Stöldskydd-associering med datorn finns i Lägga till en ny enhet.
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
-
 25
25
-
 26
26
-
 27
27
-
 28
28
-
 29
29
-
 30
30
-
 31
31
-
 32
32
-
 33
33
-
 34
34
-
 35
35
-
 36
36
-
 37
37
-
 38
38
-
 39
39
-
 40
40
-
 41
41
-
 42
42
-
 43
43
-
 44
44
-
 45
45
-
 46
46
-
 47
47
-
 48
48
-
 49
49
-
 50
50
-
 51
51
-
 52
52
-
 53
53
-
 54
54
-
 55
55
-
 56
56
-
 57
57
-
 58
58
-
 59
59
-
 60
60
-
 61
61
-
 62
62
-
 63
63
-
 64
64
-
 65
65
-
 66
66
-
 67
67
-
 68
68
-
 69
69
-
 70
70
-
 71
71
-
 72
72
-
 73
73
-
 74
74
-
 75
75
-
 76
76
-
 77
77
-
 78
78
-
 79
79
-
 80
80
-
 81
81
-
 82
82
-
 83
83
-
 84
84
-
 85
85
-
 86
86
-
 87
87
-
 88
88
-
 89
89
-
 90
90
-
 91
91
-
 92
92
-
 93
93
-
 94
94
-
 95
95
-
 96
96
-
 97
97
-
 98
98
-
 99
99
-
 100
100
-
 101
101
-
 102
102
-
 103
103
-
 104
104
-
 105
105
-
 106
106
-
 107
107
-
 108
108
-
 109
109
-
 110
110
-
 111
111
-
 112
112
-
 113
113
-
 114
114
-
 115
115
-
 116
116
-
 117
117
-
 118
118
-
 119
119
-
 120
120
-
 121
121
-
 122
122
-
 123
123
-
 124
124
-
 125
125
-
 126
126
-
 127
127
-
 128
128
-
 129
129
-
 130
130
-
 131
131
-
 132
132
-
 133
133
-
 134
134
-
 135
135
-
 136
136
-
 137
137
-
 138
138
-
 139
139
-
 140
140
-
 141
141
-
 142
142
-
 143
143
-
 144
144
-
 145
145
-
 146
146
-
 147
147
-
 148
148
-
 149
149
-
 150
150
Relaterade papper
-
ESET Smart Security Premium Användarguide
-
ESET Smart Security Premium Användarguide
-
ESET SMART SECURITY Användarguide
-
ESET SMART SECURITY Användarguide
-
ESET Endpoint Antivirus Användarguide
-
ESET Endpoint Antivirus Användarguide
-
ESET Endpoint Security Användarguide
-
ESET Endpoint Security Användarguide
-
ESET NOD32 Antivirus 15 Bruksanvisning
-
ESET Mobile Security for Android 8 Bruksanvisning






















































































































































