ESET Glossary Bruksanvisning
- Kategori
- Antivirusprogram
- Typ
- Bruksanvisning

Upphovsrätt ©2023 av ESET, spol. s r.o.
ESET Glossary har utvecklats av ESET, spol. s r.o.
För mer information besök https://www.eset.com.
Med ensamrätt. Ingen del av denna dokumentation får reproduceras, lagras i ett hämtningssystem eller överföras
i någon form eller på något sätt, elektroniskt, mekaniskt, fotokopiering, inspelning, skanning eller på annat sätt
utan skriftligt tillstånd från författaren.
ESET, spol. s r.o. förbehåller sig rätten att ändra beskriven programvara utan föregående meddelande.
Teknisk support: https://support.eset.com
REV. 2023-04-19

1 Introduktion till ESET:s ordlista 1 .........................................................................................................
1.1 Reklamprogram 1 ..........................................................................................................................
1.2 Botnet 1 .......................................................................................................................................
1.3 Falsk positiv (FP) 1 ........................................................................................................................
1.4 Packer 2 .......................................................................................................................................
1.5 Potentiellt farliga program 2 ..........................................................................................................
1.6 Potentiellt oönskade program 2 ......................................................................................................
1.7 Ransomware 6 ..............................................................................................................................
1.8 Rootkit 7 ......................................................................................................................................
1.9 Return-Oriented Programming 7 .....................................................................................................
1.10 Spionprogram 7 ..........................................................................................................................
1.11 Trojan 8 ......................................................................................................................................
1.12 Virus 8 .......................................................................................................................................
1.13 Mask 9 .......................................................................................................................................
1.14 Credential stuffing 9 ....................................................................................................................
1.15 DNS-förgiftning 9 ........................................................................................................................
1.16 DoS-attack 10 .............................................................................................................................
1.17 ICMP-attack 10 ...........................................................................................................................
1.18 Portgenomsökning 10 ..................................................................................................................
1.19 SMB-relä 10 ................................................................................................................................
1.20 TCP-desynkronisering 11 ..............................................................................................................
1.21 Maskattack 11 ............................................................................................................................
1.22 ARP-cacheattack 11 .....................................................................................................................
2 E-posthot 12 .........................................................................................................................................
2.1 Annonser 12 .................................................................................................................................
2.2 Bluffar 12 .....................................................................................................................................
2.3 Nätfiske 13 ...................................................................................................................................
2.4 Känna igen spambedrägerier 13 .....................................................................................................
2.4 Regler 14 .................................................................................................................................
2.4 Vitlista 14 .................................................................................................................................
2.4 Svartlista 14 ..............................................................................................................................
2.4 Undantag 15 ..............................................................................................................................
2.4 Kontroll på serversidan 15 ...............................................................................................................
2.5 Avancerad minnesskanner 15 .........................................................................................................
2.6 Bank- & betalskydd 15 ...................................................................................................................
2.7 Botnetsskydd 16 ...........................................................................................................................
2.8 DNA-detekteringar 16 ....................................................................................................................
2.9 ESET LiveGrid® 17 ........................................................................................................................
2.10 Kryphålsblockering 17 .................................................................................................................
2.11 Java-kryphålsblockering 18 ..........................................................................................................
2.12 ESET LiveSense 18 ......................................................................................................................
2.13 Maskininlärning 18 ......................................................................................................................
2.14 Skydd mot nätverksattacker 19 ....................................................................................................
2.15 Skydd mot ransomware 19 ...........................................................................................................
2.16 Skydd mot skriptbaserade attacker 19 ..........................................................................................
2.17 Säker webbläsare 20 ...................................................................................................................
2.18 UEFI-skanner 20 ..........................................................................................................................
2.19 Kanariefil 21 ...............................................................................................................................
2.20 Baklås 21 ...................................................................................................................................

1
Introduktion till ESET:s ordlista
ESET:s ordlista ger en heltäckande översikt över aktuella hot och ESET-tekniken som skyddar dig mot dem.
Ämnena är indelade i följande kapitel:
• Detekteringar – inkluderar datorvirus, maskar, trojanska hästar, potentiellt oönskade program och så
vidare
• Fjärrattacker – dessa hot sker via lokala nätverk eller Internet
• E-posthot – inkluderar bluffar, nätfiske, bedrägerier och så vidare.
• ESET-teknik – produktfunktioner tillgängliga i ESET:s säkerhetslösningar
Reklamprogram
Reklamprogram (även kallat adware) är reklamfinansierade program. Program som visar annonsmaterial hamnar
under den här kategorin. Reklamprogram öppnar ofta ett nytt fönster med annonser i en webbläsare eller ändrar
webbläsarens startsida. Reklamprogram levereras ofta tillsammans med gratisprogram, vilket gör att utvecklarna
kan täcka utvecklingskostnaderna för sina (ofta användbara) program.
Reklamprogram är inte farliga i sig själva – användarna störs bara av annonser. Faran ligger i att
reklamprogrammen även kan ha funktioner för spårning (som spionprogram).
Om du använder en gratisprodukt bör du vara uppmärksam under installationen. Installationsprogrammet
meddelar dig troligen om ett extra reklamprogram installeras. Ofta har du möjlighet att avbryta det och installera
programmet utan reklamprogram.
En del program går dock inte att installera utan reklamprogram eller så är funktionaliteten begränsad. Det
innebär att reklamprogram ofta kommer åt systemet på ett ”lagligt” sätt, eftersom användaren har tillåtit det. I
detta fall är det bättre att ta det säkra före det osäkra. Om en fil på datorn har identifierats som reklamprogram
rekommenderar vi att du tar bort den, eftersom sannolikheten är hög att den innehåller skadlig kod.
Botnet
En bot, eller webbrobot, är automatisk skadlig programvara som genomsöker block med nätverksadresser och
infekterar sårbara datorer. På så vis kan hackare ta kontrollen över flera datorer samtidigt och göra dem till botar
(även kallat zombier). Hackare använder vanligen botar för att infektera stora mängder datorer, vilka utgör ett
nätverk eller ett botnet. När ett botnet finns i din dator kan den användas i DDoS-attacker, som proxy och även
för att utföra automatiska åtgärder på Internet utan din kännedom (exempelvis för att skicka skräppost, sprida
virus eller stjäla personlig och privat information som bankuppgifter eller kreditkortsnummer).
Falsk positiv (FP)
I realiteten finns det ingen garanti för en 100 %-ig detekteringsgrad och det går aldrig helt att utesluta felaktig
kategorisering av rena objekt som detekteringar.

2
En falsk positiv är en ren fil eller ett rent program som felaktigt har klassificerats som skadlig kod eller ett
potentiellt oönskat program.
Packer
Komprimeringsprogram är en självuppackande körbar fil som öppnar flera sorter skadlig kod i ett enda paket.
De vanligaste komprimeringsprogrammen är UPX, PE_Compact, PKLite och ASPack. Samma skadliga kod upptäcks
på lika sätt när den komprimeras med ett annat komprimeringsprogram. Komprimeringsprogram har även
förmågan att förändra sina "signaturer" över tid, vilket gör det svårare att identifiera och ta bort skadlig kod.
Potentiellt farliga program
Det finns många legitima program som förenklar administration av datorer i ett nätverk. I fel händer kan de dock
användas i skadliga syften. ESET tillhandahåller alternativet att identifiera sådana program.
Klassificeringen Potentiellt farliga program används för kommersiell, laglig programvara. Den innefattar program
som t.ex. verktyg för fjärråtkomst, program som spårar lösenord och keylogger-program (program som registrerar
varje tangent användaren trycker ned).
Om du upptäcker att ett potentiellt farligt program körs på datorn (och du inte har installerat det) bör du
kontakta nätverksadministratören eller ta bort programmet.
Potentiellt oönskade program
Grayware eller potentiellt oönskade program (PUA; potentially unwanted application) är en bred kategori
programvara vars syfte inte är direkt skadligt, till skillnad från andra typer av skadlig kod, som virus eller trojaner.
De kan dock installera ytterligare oönskad programvara, ändra digitala enheters beteenden eller utföra aktiviteter
som inte är godkända eller inte förväntas av användaren.
Kategorier som kan klassas som grayware inkluderar programvara som visar reklam, wrappers för nedladdning,
olika verktygsfält för webbläsare, vilseledande programvara, bundleware, trackware, proxyware
(internetdelningsprogram), kryptobrytare, registerrensare (endast Windows-operativsystem) eller annan
programvara som befinner sig i någon form av gråzon eller programvara som använder otillåtna eller åtminstone
oetiska affärsmetoder (trots att de verkar legitima) och som kan förmodas vara oönskade av slutanvändare som
får veta vad programvaran skulle göra om den tilläts att installeras.
Ett potentiellt osäkert program är programvara som i sig är legitim (kanske rentav kommersiell), men som kan
missbrukas av en angripare. Detektering av dessa typer av program kan aktiveras eller inaktiveras av användare
av ESET-program.
Det finns vissa situationer där en användare kan anse att fördelarna med ett potentiellt oönskat program väger
tyngre än riskerna. Därför tilldelar ESET sådana program en lägre riskkategori jämfört med andra typer av skadliga
program, som trojaner eller maskar.
• Varning – ett potentiellt oönskat program hittades
• Inställningar

3
• Software wrappers
• Registerrensare
• Potentiellt oönskat innehåll
Anvisningar med bilder
Om du vill genomsöka och ta bort potentiellt oönskade program (PUA) i ESET Windows-hemprodukter läser
du vår artikel i ESET:s kunskapsbas.
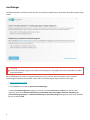
Varning – ett potentiellt oönskat program hittades
När ett potentiellt oönskat program upptäcks kan du besluta vilken åtgärd som ska vidtas:
1.Rensa/koppla från: Med det här alternativet avslutas åtgärden och det potentiellt oönskade programmet
hindras från att ta sig in i systemet.
Alternativet Koppla från visas för meddelanden om potentiellt oönskade program under hämtning från en
webbplats och alternativet Rensa för meddelanden om en fil på disk.
2.Ignorera: Med det här alternativet tillåts att ett potentiellt oönskade program kommer in i ditt system.
3.Undanta från detektering: Om du vill tillåta att den detekterade filen som redan finns på datorn körs
obehindrat på datorn i fortsättningen klickar du på Avancerade alternativ, markerar kryssrutan bredvid
Undanta från detektering och klickar på Ignorera.
4.Undanta signatur från detektering: Om du vill tillåta att alla filer som identifieras genom ett specifikt
detekteringsnamn (signatur) körs obehindrat på datorn i fortsättningen (från befintliga filer eller hämtning
från webben) klickar du på Avancerade alternativ, markerar kryssrutan bredvid Undanta signatur från
detektering och klickar på Ignorera. Om fler detekteringsfönster med samma detekteringsnamn visas
omedelbart efteråt klickar du på Ignorera för att stänga dem (eventuella ytterligare fönster är relaterade till
en detektering som inträffade innan signaturen undantogs från detektering).

4
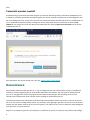
Inställningar
När ESET-produkten installeras kan du välja om du vill aktivera detektering av potentiellt oönskade program enligt
nedan:
Varning
Potentiellt oönskade program kan installera reklamprogram, verktygsfält eller andra oönskade och osäkra
programfunktioner.
Dessa inställningar kan ändras i programinställningarna när som helst. Om du vill aktivera eller inaktivera
detekteringen av potentiellt oönskade, osäkra eller misstänkta program följer du dessa anvisningar:
1. Öppna din ESET-produkt.
2. Tryck på F5 för att komma åt Avancerade inställningar.
3. Klicka på Detekteringsmotor (i tidigare versioner även kallat Antivirus eller Dator) och aktivera eller
inaktivera alternativen Aktivera detektering av potentiellt oönskade program, Aktivera detektering av
potentiellt farliga program och Aktivera detektering av misstänkta program enligt dina preferenser. Bekräfta
genom att klicka på OK.

5
Anvisningar med bilder
Mer utförliga anvisningar om hur du konfigurerar produkter för att detektera eller ignorera potentiellt
oönskade program finns i olika artiklar i ESET:s kunskapsbas:
• ESET NOD32 Antivirus / ESET Internet Security / ESET Smart Security Premium
• ESET Cyber Security för macOS/ESET Cyber Security Pro för macOS
• ESET Endpoint Security / ESET Endpoint Antivirus for Windows
• ESET Mobile Security för Android
Software wrappers
En software wrapper är en särskilt typ av programmodifiering som används av vissa fildelningsplatser. Det är ett
verktyg från tredje part som installerar programmet du avsåg att hämta, men även ytterligare programvara som
verktygsfält eller reklamprogram. Den ytterligare programvaran kan även ändra webbläsarens startsida och
sökinställningar. Dessutom meddelar fildelningsplatser ofta inte programleverantören eller den som hämtar
programmet om att modifieringar gjorts och döljer ofta alternativ för att välja bort modifieringen. Därför
klassificerar ESET software wrappers som en typ av potentiellt oönskat program, så att användare kan välja om
hämtningen ska godkännas eller inte.
Registerrensare
Registerrensare är program som kan föreslå att Windows-registrets databas kräver regelbundet underhåll eller
rensning. Att använda en registerrensare kan införa vissa risker i datorsystemet. Dessutom gör vissa
registerrensare okvalificerade påståenden som inte kan verifieras eller på annat sätt stödjas om sina fördelar
och/eller genererar vilseledande rapporter om ett datorsystem baserat på resultaten av en ”kostnadsfri
genomsökning”. Dessa vilseledande påståenden och rapporter försöker övertyga dig att köpa en fullständig
version eller en prenumeration, vanligen utan att du får utvärdera registerrensaren före betalningen. Av dessa
skäl klassificerar ESET sådana program som potentiellt oönskade och ger dig möjlighet att tillåta eller blockera

6
dem.
Potentiellt oönskat innehåll
Om detektering av potentiellt oönskade program är aktiverad i din ESET-produkt, så blockeras webbplatser som
är kända för att främja potentiellt oönskade program eller för att vilseleda användare till att utföra åtgärder som
kan vara skadliga för deras system eller surfande som potentiellt oönskat innehåll. Om du får ett meddelande om
att en webbplats du försöker besöka är kategoriserad som potentiellt oönskat innehåll kan du klicka på Gå
tillbaka för att navigera bort från den blockerade webbsidan eller klicka på Ignorera och fortsätt om du vill låta
webbplatsen läsas in.
Mer information om det här ämnet finns i den här artikeln i ESET:s kunskapsbas.
Ransomware
Ransomware (kallas även filkrypterare) är en typ av skadlig kod som låser enheten eller krypterar innehållet på
enheten och kräver dig på pengar för att återställa åtkomsten till innehållet. Den här typen av skadlig kod kan
även ha en inbyggd timer med en förprogrammerad sluttid för betalningen. Om betalning inte sker innan
sluttiden höjs beloppet eller så blir enheten till slut omöjlig att återfå åtkomsten till.
När enheten infekteras kan filkrypteraren försöka kryptera de delade enheterna på enheten. Den här processen
kan se ut som att den skadliga koden sprider sig i nätverket, men egentligen gör den inte det. Den här situationen
uppstår när den delade enheten på en filserver krypteras, men själva servern inte har infekterats med skadlig kod
(om den inte är en terminalserver).
Skapare av ransomware genererar ett nyckelpar, en publik och en privat, och placerar den publika i den skadliga

7
koden. Själva ransomwaren kan ingå i en trojansk häst eller se ut som en fil eller en bild som du kan få i ett e-
postmeddelande, på sociala medier eller i chattprogram. Efter att ha infiltrerat datorn genererar den skadliga
koden en slumpmässig symmetrisk nyckel och krypterar enhetens data. Den publika nyckeln i den skadliga koden
används för att kryptera den symmetriska nyckeln. Meddelandet med betalningskravet som visas på enheten kan
vara en falsk varning om att systemet har använts för olagliga ändamål eller innehåller olagligt innehåll. Offret för
ransomwaren uppmanas att betala lösensumman via olika betalningsmetoder. Alternativen är ofta sådana som är
svåra att spåra, till exempel digitala valutor (kryptovalutor), SMS med höga avgifter eller värdekuponger. Efter att
ha fått betalningen ska skaparen av ransomwaren låsa upp enheten eller använda sin privata nyckel för att
dekryptera den symmetriska nyckeln och dekryptera offrets data, men det finns inga garantier för detta.
Mer information om skydd mot ransomware
ESET:s produkter använder teknik i flera lager som skyddar enheter mot ransomware. Läs i vår artikel i
ESET:s kunskapsbas om hur du bäst skyddar systemet mot ransomware.
Rootkit
Rootkit är skadliga program som ger Internetangripare obegränsad tillgång till ett system, samtidigt som deras
närvaro förblir dold. När ett rootkit har använts för att komma åt en dator (oftast genom att utnyttja en sårbarhet
i systemet) används funktioner i operativsystemet som gör att antivirusprogram inte upptäcker detta. Processer,
filer och data i Windowsregistret döljs. På grund av detta är det nästan omöjligt att upptäcka angreppet med
vanliga testtekniker.
Det finns två detekteringsnivåer för att förhindra rootkits:
1.Vid försök till åtkomst till ett system: Rootkiten finns fortfarande inte i datorn och är därför inaktiva. De
flesta antivirussystem kan eliminera rootkit på den här nivån (förutsatt att de verkligen detekterar att
sådana filer infekteras).
2.När de är dolda från vanlig genomsökning: ESET-användare har fördelen av Anti-Stealth-tekniken som
även kan identifiera och eliminera aktiva rootkit.
Return-Oriented Programming
Return-Oriented Programming (ROP) är en typisk kodåteranvändningsattack, där en angripare dirigerar
kontrollflödet genom befintlig kod med ett skadligt resultat. En ROP-attack representerar en avancerad version av
en stack-smashing-attack. Ett stackbuffertspill inträffar när ett program skriver till en minnesadress på
programmets anropsstack utanför den avsedda datastrukturen, vanligtvis med en buffert med fast längd.
ROP är en exploateringsteknik som möjliggör körning av kod på målsystemet. Genom att få kontroll över
anropsstacken kontrollerar angriparen flödet för befintlig betrodd programvara som körs på datorn och
manipulerar den för att utföra en annan uppgift än vad som var avsett.
Spionprogram
Den här kategorin innehåller alla program som skickar privat information utan att användaren är medveten om
det eller har gett sin tillåtelse. Spionprogram använder funktioner för spårning till att skicka olika typer av
statistiska data, till exempel en lista med besökta webbplatser, e-postadresser från användarens kontaktlista eller
en lista med registrerade tangenttryckningar.

8
Författarna till spionprogram hävdar att dessa tekniker har som mål att ta reda på mer om användarnas behov
och intressen för att på så sätt möjliggöra bättre riktade annonser. Problemet är att det inte finns någon tydlig
gräns mellan användbara och skadliga program och att det inte går att vara säker på att informationen inte
kommer att missbrukas. Data som hämtas med hjälp av spionprogram kan innehålla lösenord, PIN-koder,
bankkontonummer och så vidare. Skapare av program skickar ofta med spionprogram tillsammans med en
gratisversion av programmet för att tjäna pengar eller för att göra det önskvärt att betala för programmet. Ofta
informeras användarna om förekomsten av spionprogram under installationen så att de får en anledning att
uppgradera till en betald version utan spionprogrammet.
Exempel på välkända gratisprodukter som levereras tillsammans med spionprogram är klientprogram för P2P-
nätverk (serverlösa nätverk). Spyfalcon och Spy Sheriff (och många andra) tillhör en specifik underkategori av
spionprogram – de utger sig för att vara antispionprogram men är själva spionprogram.
Om en fil identifieras som spionprogram på datorn rekommenderar vi att ta bort den, eftersom sannolikheten är
hög att den innehåller skadlig kod.
Som en underkategori till spionprogram kan keyloggers vara maskin- eller programvarubaserade.
Programvarubaserade keyloggers kan endast samla in informationen som skrivs in på en enskild webbplats eller
program. Mer sofistikerade keyloggers kan registrera allt du skriver, inklusive den information du kopierar/klistrar
in. Vissa keyloggers för angrepp mot mobila enheter kan spela in samtal, information från meddelandeprogram,
platser eller till och med mikrofon- och kamerainspelningar.
Trojan
Från början definierades trojaner (trojanska hästar) i datorsammanhang som en klass av hot som utger sig för att
vara användbara program och på så sätt lurar användare att köra dem.
Eftersom trojaner är en mycket omfattande kategori delas den ofta in i flera underkategorier:
• Hämtare – skadliga program som hämtar andra infiltreringar från Internet.
• Spridare – skadliga program som kan lägga in andra typer av skadlig kod på smittade datorer.
• Bakdörr – skadliga program som kommunicerar med fjärrangripare och låter dem få tillgång till datorn och
ta kontroll över den.
• Keylogger – (tangentloggare) – ett program som registrerar varje tangent som användaren trycker på och
skickar denna information till fjärrangripare.
• Uppringningsprogram – skadliga program som får datorn att ringa upp dyra betalnummer. Det är nästan
omöjligt för en användare att upptäcka att en ny anslutning skapades. Uppringningsprogram kan endast
orsaka skada tillsammans med modem för uppringda anslutningar, vilket nästan inte används längre.
Om en fil på datorn har identifierats som en trojan, rekommenderar vi att du tar bort den, eftersom den troligen
innehåller skadlig kod.
Virus
Ett datorvirus är ett stycke skadlig kod som läggs till befintliga filer på din dator. Virus har fått sitt namn efter
biologiska virus, eftersom de sprider sig mellan olika platser på ungefär samma sätt. Termen ”virus” används ofta
felaktigt som namn på alla typer av hot. Denna användning försvinner gradvis och byts ut mot den mer korrekta

9
termen ”skadlig kod” (skadlig programvara).
Datorvirus angriper huvudsakligen körbara filer och dokument. I korthet fungerar ett datorvirus så här: efter
körning av en infekterad fil, anropas den skadliga koden och körs innan det ursprungliga programmet körs. Ett
virus kan infektera alla filer som den aktuella användaren har skrivbehörighet till.
Hur aktiva och allvarliga datorvirus är varierar. Vissa av dem är extremt farliga eftersom de avsiktligt kan ta bort
filer från en hårddisk. Å andra sidan finns det virus som inte orsakar någon verklig skada. De är endast avsedda att
irritera användaren och demonstrera författarnas tekniska kunskaper.
Om datorn infekterats med ett virus och det inte går att rensa, skicka det till ESET:s forskningslabb för
undersökning. I en del fall ändras infekterade filer i en sådan grad att rensning inte är möjlig och filerna måste
bytas ut mot rena kopior.
Mask
En datormask är ett program som innehåller skadlig kod och som attackerar värddatorer och sprider sig via
nätverk. Den huvudsakliga skillnaden mellan ett virus och en mask är att maskar själva kan sprida sig - de är inte
beroende av värdfiler (eller startsektorer). Maskar sprids till e-postadresser i din kontaktlista eller utnyttjar
sårbarheter i säkerheten hos nätverksprogram.
Maskar är därför mer livskraftiga än datorvirus. På grund av Internets tillgänglighet kan de inom några timmar
eller till och med minuter från att de släpps spridas över hela världen. Denna förmåga att snabbt sprida sig själva
gör maskar farligare än andra typer av skadlig programvara.
En mask som har aktiverats på en dator kan orsaka ett antal olika problem: Den kan ta bort filer, försämra datorns
prestanda eller till och med inaktivera vissa program. Sättet på vilket maskar fungerar gör det möjligt för dem att
fungera som ”transportmedel” för andra typer av infiltreringar.
Om datorn infekteras av en mask rekommenderar vi att ta bort de infekterade filerna, eftersom de troligen
innehåller skadlig kod.
Credential stuffing
Credential stuffing är en cyberattack som använder data från läckta databaser med inloggningsuppgifter.
Angripare använder botar och andra automatiseringsmetoder för att logga in på konton på många webbplatser
med hjälp av läckt data. Angripare utnyttjar användare som återanvänder sina inloggningsuppgifter på flera
webbplatser och tjänster. När attacken lyckas kan angripare få full åtkomst till kontot och användarnas data som
lagras på kontot. Angripare kan utnyttja denna åtkomst för att stjäla personuppgifter för att identitetsstöld,
bedrägliga transaktioner, spridning av spam eller andra skadliga åtgärder.
DNS-förgiftning
Med DNS-förgiftning (Domain Name Server) lurar hackare DNS-servern till en dator att tro att den falska
information hackarna anger är korrekt och autentisk. Den falska informationen cachas en viss tidsperiod och gör
det möjligt för sabotörer att skriva om IP-adressers DNS-svar. Det innebär att användare som försöker komma åt
webbplatser på Internet hämtar datorvirus eller maskar i stället för det ursprungliga innehållet.

10
DoS-attack
DoS eller Denial of Service, är ett försök att göra en dator eller ett nätverk oåtkomligt för sina avsedda användare.
Kommunikationen mellan drabbade användare förhindras och går inte längre att upprätthålla. Datorer som
utsätts för DoS-attacker måste vanligtvis startas om för att fungera korrekt.
I de flesta fall är målen webbservrar och syftet är att göra dem otillgängliga för användare under en viss tid.
ICMP-attack
ICMP (Internet Control Message Protocol) är ett populärt och vanligt Internetprotokoll. Det används främst av
nätverksanslutna datorer för att skicka olika felmeddelanden.
Fjärrangripare försöker utnyttja svagheterna i ICMP-protokollet. ICMP-protokollet är gjort för
envägskommunikation som inte kräver autentisering. Det gör att fjärrangripare kan utlösa så kallade DoS-attacker
(Denial of Service) eller attacker som ger obehöriga tillgång till inkommande och utgående paket.
Typiska exempel på ICMP-attacker är ping-flood, ICMP_ECHO-flood och smurfattacker. Datorer som utsätts för
ICMP-attacken är mycket långsammare (det gäller alla program som använder Internet) och har problem att
ansluta till Internet.
Portgenomsökning
Portgenomsökning används för att avgöra vilka datorportar som är öppna på en nätverksvärd. En portskanner är
ett program som hittar dessa portar.
En datorport är en virtuell punkt som hanterar inkommande och utgående data, vilket är mycket viktigt ur
säkerhetssynpunkt. I ett stort nätverk kan information som samlas in av portskannrar hjälpa till att identifiera
potentiella sårbarheter. Sådan användning är legitim.
Portgenomsökning används dock ofta av hackare som försöker skada säkerheten. Deras första steg är att skicka
paket till alla portar. Beroende på svarstypen går det att avgöra vilka portar som används. Själva genomsökningen
ger inte upphov till några skador, men du bör vara medveten om att denna aktivitet kan identifiera potentiella
sårbarheter och tillåta att angripare tar kontrollen över fjärrdatorer.
Det rekommenderas att nätverksadministratörer blockerar alla oanvända portar och skyddar de som används från
obehörig åtkomst.
SMB-relä
SMB Relay och SMB Relay 2 är speciella program som kan genomföra angrepp mot fjärrdatorer. Programmen
utnyttjar fildelningsprotokollet SMB (Server Message Block) som ligger ovanpå NetBIOS. En användare som delar
en eller katalog på det lokala nätverket använder troligen detta fildelningsprotokoll.
Inom den lokala nätverkskommunikationen utväxlas hash-värden för lösenord.
SMB Relay tar emot en anslutning på UDP-portarna 139 och 445 och vidarebefordrar paketen som skickas mellan
klienten och servern samt modifierar dem. När anslutningen och autentiseringen har utförts kopplas klienten

11
bort. SMB Relay skapar en ny virtuell IP-adress. Det går att få åtkomst till den nya adressen med kommandot ”net
use \\192.168.1.1”. Därefter kan adressen användas av alla nätverksfunktioner i Windows. SMB Relay
vidarebefordrar kommunikation med SMB-protokollet förutom förhandling och autentisering. Fjärrangripare kan
använda IP-adressen så länge klientdatorn är ansluten.
SMB Relay 2 fungerar enligt samma princip som SMB Relay, förutom att det använder NetBIOS-namn i stället för
IP-adresser. Båda kan utföra man-in-the-middle-attacker. Dessa angrepp gör det möjligt för fjärrangripare att läsa,
infoga och ändra meddelanden som utväxlas mellan två kommunikationsslutpunkter utan att upptäckas. Datorer
som utsätts för sådana angrepp slutar ofta svara eller startar oväntat om.
Vi rekommenderar att undvika angrepp genom att använda autentiseringslösenord eller nycklar.
TCP-desynkronisering
TCP-desynkronisering är en teknik som används i TCP-kapningsattacker. Den utlöses av en process i vilken det
sekventiella numret på inkommande paket skiljer sig från det förväntade sekventiella numret. Paket med ett
oväntat sekventiellt nummer avvisas (eller lagras i en buffert om de visas i det aktuella kommunikationsfönstret).
I desynkronisering avvisar båda kommunikationsslutpunkterna mottagna paket som ger fjärrangripare möjlighet
att infiltrera och tillhandahålla paket med korrekt sekventiellt nummer. Angriparna kan även manipulera eller
ändra kommunikation.
TCP-kapningsattacker försöker avbryta kommunikation mellan server och klient eller serverlös kommunikation.
Det går att undvika många angrepp genom att använda autentisering för alla TCP-segment. Du bör också använda
rekommenderade konfigurationer för nätverksenheter.
Maskattack
En datormask är ett program som innehåller skadlig kod och som attackerar värddatorer och sprider sig via ett
nätverk. Nätverksmaskar utnyttjar sårbarheter i säkerheten hos olika program. På grund av Internets tillgänglighet
kan de spridas över hela världen inom några timmar från det att de släpps.
Det går att undvika de flesta maskangrepp (Sasser, SqlSlammer) genom att använda standardinställningarna för
säkerhet i brandväggen, eller genom att blockera oskyddade och oanvända portar. Det är även nödvändigt att
operativsystemet uppdateras med de senaste säkerhetskorrigeringsfilerna.
ARP-förgiftningsattack
ARP (Address Resolution Protocol) översätter mellan adresser på datalänklagret (MAC-adresser) och
nätverkslagret (IP-adresser). En förgiftningsattack mot ARP-cachen gör det möjligt för angripare att fånga upp
kommunikation mellan nätverksenheter genom att skada nätverkets ARP-tabeller (MAC-till-IP-
enhetsmappningar).
Angriparen skickar ett falskt ARP-svarsmeddelande till nätverkets standardgateway och informerar om att MAC-
adressen är associerad med ett annat måls IP-adress. När standardgatewayen tar emot det här meddelandet och
sänder ändringarna till alla andra enheter i nätverket går all målets trafik till alla andra nätverksenheter via
angriparens dator. Den här åtgärden gör att angriparen kan inspektera eller ändra trafiken innan den
vidarebefordras till den avsedda destinationen.

12
E-posthot
E-post är en form av kommunikation som har många fördelar.
Dessvärre gör e-postens och internets höga anonymitetsnivå att det finns utrymme för olagliga aktiviteter som
skräppost, s.k. spam. Skräppost, eller spam, inkluderar oönskade annonser, bluffar och spridning av skadlig
programvara – skadlig kod. Det blir ännu mer besvärligt och farligt för användaren genom att det kostar mycket
lite att skicka spam och spammare har många verktyg och källor för att hitta nya e-postadresser. Dessutom är
spam mycket svårt att reglera eftersom det finns så mycket och den är så mångskiftande. Ju längre du använder
din e-postadress, desto högre sannolikhet att den hamnar i en databas i ett spamprogram.
Några tips för att förhindra spam:
• Publicera om möjligt inte din e-postadress på Internet
• Ge bara din e-postadress till personer du litar på
• Använd om möjligt inte vanliga alias – med mer invecklade alias blir det mindre sannolikt att de hittar dig
• Svara inte på spam som har hamnat i din inkorg
• Var försiktig när du fyller i formulär på Internet – var extra försiktig med kryssrutor som ”Ja, jag vill ha
information om”.
• Använd ”specialiserade” e-postadresser, t.ex. en till arbetet, en annan till att skriva till vänner osv.
• Ändra din e-postadress regelbundet
• Använd en antispamlösning
Annonser
Annonsering på Internet är en av de annonseringsformer som växer snabbast. De största fördelarna när det gäller
marknadsföring är minimala kostnader samt en hög riktningsnivå. Dessutom levereras annonserna nästan
omedelbart. Många företag använder marknadsföring via e-post för effektiv kommunikation med både befintliga
och potentiella kunder.
Denna annonseringsmetod är legitim, eftersom användaren kan vara intresserad av att få reklam om vissa
produkter. Men många företag skickar oönskad reklam via e-post. I sådana fall går e-postannonsering över
gränsen och blir spam.
Mängden oönskad e-post har blivit ett problem och visar inga tecken på att avta. Författare till oönskad e-post
försöker maskera spam som legitima meddelanden.
Bluffar
En bluff (hoax) är felinformation som sprids via Internet. Bluffar sprids vanligen med e-post och
kommunikationsverktyg som ICQ och Skype. Själva meddelandet är ofta ett skämt eller en vandringssägen.
Bluffar genom datorvirus försöker ofta skapa rädsla, osäkerhet och tvivel (FUD) hos mottagarna och få dem att tro

13
att det finns ett ”oupptäckbart virus” som tar bort filer och hämtar lösenord eller utför andra skadliga åtgärder på
datorsystemet.
En del bluffar fungerar genom att mottagarna ombeds att vidarebefordra meddelandena till sina kontakter, vilket
håller bluffen levande. Det finns mobiltelefonbluffar, vädjanden om hjälp, folk som erbjuder sig att skicka dig
pengar från andra länder osv. I de flesta fall är det omöjligt att veta avsikten.
Om du får ett meddelande som ber dig vidarebefordra det till alla du känner kan det mycket väl vara en bluff. Det
finns många webbplatser på Internet som verifierar att ett e-postmeddelande är äkta. Sök på Internet om alla
meddelanden du misstänker kan vara bluffar innan du vidarebefordrar dem.
Nätfiske
Termen nätfiske (phishing) definierar en kriminell teknik där användare manipuleras att lämna ifrån sig
konfidentiell information. Målet är att få tillgång till känsliga data som bankkontonummer, PIN-koder och så
vidare.
Detta sker oftast genom att någon skickar ett e-postmeddelande och utger sig för att vara en trovärdig person
eller företag (t.ex. en finansinstitution, ett försäkringsbolag eller liknande). E-postmeddelandet kan verka äkta och
det kan innehålla grafik och innehåll som ursprungligen kommer från källan som imiteras. Du ombeds under olika
förevändningar (verifiering av uppgifter, finansiella åtgärder) att ange en del personliga uppgifter – kontonummer
eller användarnamn och lösenord. Alla sådana data kan lätt stjälas och missbrukas om de anges.
Tänk på att banker, försäkringsbolag och andra legitima företag aldrig begär användarnamn eller lösenord via
oönskad e-post.
Känna igen spambedrägerier
Det finns några allmänna kännetecken som kan hjälpa dig identifiera spam (oönskad e-post) i inkorgen. Om ett
meddelande uppfyller några av följande villkor är det troligen ett spammeddelande.
• Avsändaradressen tillhör inte någon på din kontaktlista.
• Du blir erbjuden en stor summa pengar men måste först skicka en mindre summa.
• Med olika förevändningar (verifiering av data, finansiella aktiviteter, osv.) uppmanas du att ange
personliga data, till exempel bankkontonummer, användarnamn eller lösenord.
• Meddelandet är skrivet på ett främmande språk.
• Du ombeds köpa en produkt du inte är intresserad av. Om du bestämmer dig för att köpa den ändå bör du
kontrollera att meddelandets avsändare är en pålitlig försäljare (kontrollera detta med produktens
tillverkare).
• Vissa ord är felstavade i ett försök att lura spamfiltret, till exempel ”vaigra” istället för ”viagra”.

14
Regler
När det handlar om antispamlösningar och e-postklienter kan regler manipulera e-postfunktioner. De består av
två logiska delar:
1.Villkor (exempelvis ett inkommande meddelande från en viss adress eller med ett visst e-postämne)
2.Åtgärd (exempelvis att ta bort meddelandet eller flytta det till en viss mapp).
Olika antispamlösningar har olika många regler och de kan kombineras på olika sätt. Dessa regler skyddar mot
spam (oönskad e-post). Typiska exempel:
1. Villkor: Ett inkommande e-postmeddelande innehåller vissa ord som normalt förekommer i spammeddelanden
2. Åtgärd: Ta bort meddelandet
1. Villkor: Ett inkommande e-postmeddelande innehåller en bifogad fil med tillägget .exe
2. Åtgärd: Ta bort den bifogade filen och leverera meddelandet
1. Villkor: Ett inkommande e-postmeddelande ankommer från din arbetsgivare
2. Åtgärd: Flytta meddelandet till mappen Arbete
För att underlätta administrationen och filtrera spam mer effektivt rekommenderar vi att använda en
kombination av reglerna i antispamprogram.
Vitlista
I allmänhet är en vitlista en lista med objekt eller personer som har accepterats, eller som har fått behörighet. En
”vitlista för e-post” (tillåtna adresser) anger en lista med kontakter som användaren vill ta emot meddelanden
från. Sådana vitlistor baseras på nyckelord som förekommer i e-postadresser, domännamn eller IP-adresser.
Om en vitlista fungerar i exklusivt läge går det inte att ta emot meddelanden från någon adress, domän eller IP-
adress som inte förekommer i listan. Om vitlistan inte är exklusiv tas sådana meddelanden inte bort, utan filtreras
på något annat sätt.
En vitlista baseras på en princip som är motsatt den för en svartlista. Vitlistor är relativt enkla att underhålla,
särskilt jämfört med svartlistor. Det rekommenderas att du använder både vitlistor och svartlistor så att
spamfiltreringen blir så effektiv som möjligt.
Svartlista
En svartlista är vanligtvis en lista med oacceptabla eller förbjudna objekt eller personer. I den virtuella världen är
det en teknik som gör att det går att acceptera meddelande från alla användare som inte finns med i en sådan
lista.

15
Det finns två typer av svartlistor: Listor som skapas av användare i deras antispamprogram och professionella
svartlistor på Internet som skapas av specialiserade organisationer och uppdateras regelbundet.
Det är nödvändigt att använda svartlistor för framgångsrik spamfiltrering, men de är mycket svåra att underhålla
eftersom nya objekt som ska blockeras tillkommer varje dag. Vi rekommenderar att använda både vitlistor och
svartlistor så att spamfiltreringen blir så effektiv som möjligt.
Undantag
Undantagslistan (kallas även listan över undantag) innehåller vanligen e-postadresser som kan vara bedrägliga
och användas till spam. E-postmeddelanden med avsändarens adress i undantagslistan genomsöks alltid efter
spam. Som standard innehåller undantagslistan dina e-postadresser från befintliga e-postklientkonton.
Kontroll på serversidan
Kontroll på serversidan är en teknik som gör det möjligt att identifiera massutskickad spam baserat på antalet
mottagna meddelanden och på användarnas reaktioner. Varje meddelande lämnar kvar ett unikt digitalt
”fingeravtryck” baserat på innehållet i meddelandet. Det unika ID-numret säger inget om e-postmeddelandets
innehåll. Två identiska meddelanden får identiska fingeravtryck, medan olika meddelanden får olika fingeravtryck.
Om ett meddelande markeras som spam skickas dess fingeravtryck till servern. Om servern tar emot fler identiska
fingeravtryck (som motsvarar ett visst spammeddelande) lagras fingeravtryck i databasen med spamavtryck. Vid
genomsökning av inkommande meddelanden skickar programmet meddelandenas fingeravtryck till servern.
Servern returnerar information om vilka fingeravtryck som motsvarar meddelanden som redan har markerats
som spam av användarna.
Avancerad minnesskanner
Avancerad minnesskanner fungerar i kombination med Kryphålsblockering för att stärka skyddet mot skadlig
programvara som har utformats för att kringgå detekteringen genom skadlig programvara vid användning av
förvridning och/eller kryptering. I fall där standardmässig emulering eller heuristik kanske inte upptäcker ett hot
kan den avancerade minnesskannern identifiera misstänkligt beteende och skanna hot när de avslöjas i
systemminnet. Den här lösningen är effektiv även mot tungt mörklagd skadlig programvara.
Till skillnad från hos kryphålsskyddet är den avancerade minnesskannern en metod för verkställande i efterhand,
som innebär att det finns risk för att viss skadlig aktivitet kan har inträffat före detekteringen av ett hot; men i de
fall där andra detekteringstekniker har misslyckats erbjuds ett extra säkerhetslager.
Bank- & betalskydd
Bank- & betalskydd är ett ytterligare skyddslager utformat för att skydda dina finansiella data under
onlinetransaktioner.
ESET Smart Security Premium och ESET Internet Security innehåller en inbyggd lista med fördefinierade
webbplatser som får en Säker webbläsare att öppnas. Du kan lägga till en webbplats eller redigera listan med
webbplatser i produktkonfigurationen.
Aktivera Säkra alla webbläsare för att starta alla webbläsare som stöds i ett säkert läge.

16
För mer information om funktionen, se följande artiklar i ESET:s kunskapsbas:
• Hur använder jag ESET:s bank- och betalningsskydd?
• Pausa eller inaktivera Bank- och betalningsskydd i ESET:s Windows-hemprodukter
• ESET Bank- och betalningsskydd, vanliga fel
Användning av krypterad HTTPS-kommunikation är nödvändig för att kunna surfa säkert. Bank- & betalskydd
stöds av följande webbläsare:
• Internet Explorer 8.0.0.0
• Microsoft Edge 83.0.0.0
• Google Chrome 64.0.0.0
• Firefox 24.0.0.0
Öppna Bank- & betalskydd i önskad webbläsare
När du öppnar Bank- & betalskydd direkt från fliken Verktyg på produktmenyn, så öppnas det i den webbläsare
som har angetts som standard i Windows. Annars, när du öppnar din föredragna webbläsare (inte från
produktmenyn), så kommer webbplatser från listan över skyddade webbplatser att omdirigeras till samma typ av
webbläsare som skyddas av ESET.
Botnetsskydd
Botnetskyddet upptäcker skadlig kod genom att analysera nätverkets kommunikationsprotokoll. Botnet-
programvara ändras frekvent i motsats till nätverksprotokoll, som inte har ändrats de senaste åren. Den här nya
tekniken hjälper ESET att bekämpa skadlig programvara som försöker undgå detektering och försöker ansluta din
dator till botnet-nätverk.
DNA-detekteringar
Detekteringstyperna sträcker sig från mycket specifika hash-värden till ESET:s DNA-detekteringar, som är
komplexa definitioner av skadliga beteenden och egenskaper för skadliga program. Medan skadliga program
enkelt kan modifieras eller förvridas av angripare, så kan objektens beteenden inte ändras så lätt, vilket DNA-
detekteringarna är utformade för att utnyttja.
Vi utför djup analys av koden och extraherar ”gener” som ligger bakom dess beteende och konstruerar DNA-
detekteringar som används för att bedöma potentiellt misstänkt kod, oavsett om den påträffas på disken eller i
processminnet. DNA-detekteringar kan identifiera prover av vissa kända skadliga program, nya varianter av en
familj med skadliga program eller till och med tidigare osedda eller okända skadliga program som innehåller gener
som tyder på skadliga beteenden.

17
ESET LiveGrid®
ESET LiveGrid® (bygger på ESET ThreatSense.Netavancerat varningssystem) använder data som ESET:s användare
har skickat jorden runt och skickat dem till ESET:s forskningslabb. Genom att erbjuda prov på misstänkt material
och metadata från verkligheten gör ESET LiveGrid® det möjligt för oss att reagera omedelbart på våra kunders
behov och hålla ESET uppmärksamma på de senaste hoten.
ESET:s forskare inom skadlig kod använder informationen för att skapa en korrekt ögonblicksbild av naturen och
omfattningen av globala hot, som hjälper oss att fokusera på rätt mål. ESET LiveGrid®-data spelar en viktig roll när
det gäller inställningsprioriteringarna i vår automatiserade bearbetning.
Dessutom implementeras ett ryktessystem som bidrar till att förbättra den övergripande effektiviteten för våra
lösningar när det gäller skydd mot skadlig kod. Användaren kan kontrollera ryktet för filer och processer som körs
direkt från programmets gränssnitt eller kontextmeny med ytterligare information från ESET LiveGrid®. När en
exe-fil eller arkiveringsfil undersöks i en användares system jämförs dess hashtagg först mot en databas med vit-
och svartlistade objekt. Om den hittas i vitlistan betraktas den inspekterade filen som ren och flaggas för att
uteslutas från framtida genomsökningar. Om den är på svartlistan vidtas lämpliga åtgärder baserat på hotets
karaktär. Om ingen träff hittas skannas filen noggrant. Baserat på resultaten i den här genomsökningen
kategoriseras filerna som hot eller icke-hot. Den här metoden har en signifikant positiv påverkan på
genomsökningsprestanda. Det här ryktessystemet möjliggör effektiv detektering av prover med skadlig
programvara även innan deras signaturer levereras till användarens dator via en uppdaterad virusdatabas (vilket
sker flera gånger om dagen).
Utöver ESET LiveGrid®-systemet, så samlar ESET LiveGrid®-feedbacksystemet in information om din dator som är
kopplad till nyupptäckta hot. Informationen kan bestå av ett exempel eller en kopia av filen som innehåller hotet,
sökvägen till filen, filnamnet, datum och tid, sättet på vilket hotet uppträdde på datorn samt information om
datorns operativsystem.
ESET LiveGrid®-servrar
Våra ESET LiveGrid®-servrar finns i Bratislava, Wien och San Diego. De är dock endast servar som svarar på
förfrågningar från kunderna. Inskickade prover behandlas i Bratislava i Slovakien.
Aktivera eller inaktivera ESET LiveGrid® i ESET-produkter
Mer utförliga och illustrerade anvisningar om hur du aktiverar eller inaktiverar ESET LiveGrid® i ESET-
produkter finns i vår artikel i ESET:s kunskapsbas.
Kryphålsblockering
Kryphålsblockeringen är utformad för att förstärka ofta exploaterade programtyper, såsom webbläsare, PDF-
läsare, e-postklienter och Microsoft Office-komponenter samt skydda mot ROP-attacker. Kryphålsblockeringen är
tillgänglig och aktiverat som standard i alla ESET-hemprodukter för Windows, ESET-produkter för Windows Server
och ESET-endpoint-produkter för Windows.
Det arbetar genom att övervaka beteende i processerna för misstänklig aktivitet som kan indikera ett kryphål.
När kryphålsblockeringen identifierar en misstänkt process stoppar den omedelbart processen och registrerar och
skickar data om hotet till ESET LiveGrid®-molnsystemet. Denna data bearbetas av ESET:s forskningslabb och
används för att bättre skydda alla användare mot okända hot och dagnollattacker (nyligen publicerad skadlig kod
utan någon förkonfigurerad åtgärd).
Sidan laddas...
Sidan laddas...
Sidan laddas...
Sidan laddas...
-
 1
1
-
 2
2
-
 3
3
-
 4
4
-
 5
5
-
 6
6
-
 7
7
-
 8
8
-
 9
9
-
 10
10
-
 11
11
-
 12
12
-
 13
13
-
 14
14
-
 15
15
-
 16
16
-
 17
17
-
 18
18
-
 19
19
-
 20
20
-
 21
21
-
 22
22
-
 23
23
-
 24
24
ESET Glossary Bruksanvisning
- Kategori
- Antivirusprogram
- Typ
- Bruksanvisning
























